Case 1
Refer to the exhibit.
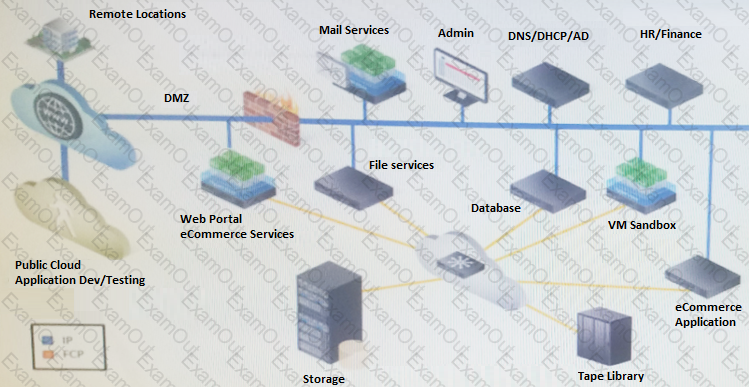
Your company recently negotiated several contracts with new customers to use its proprietary eCommerce system. As a result, the customer base has grown rapidly, which has introduced several challenges and requirements.
Business requirements:
Applications need to scale quickly
Metrics and reporting to anticipate business trends and efficient use of resources
External customers are looking to license the eCommerce application
Other considerations:
Applications need to be recorded for the public cloud
Address security vulnerabilities for customer data in the cloud
Refer to Case 1.
You are designing a Do-It-Yourself private cloud solution. What is the recommended way to provide
applications the ability to scale quickly?
What is a deliverable of the cloud design process?
An organization wants to provide its developers the ability to deploy VMs. These VMs have software and
libraries installed that are used to develop applications. Each VM will be configured with the same IP address
and will be able to download application code from a central server.
What will be included in the design to support these requirements?
An organization wants to deploy cloud applications using block storage. The architect has included a HCI
solution in the cloud design. Which requirements must have led to including this solution in the design?
Case 1
Refer to the exhibit.
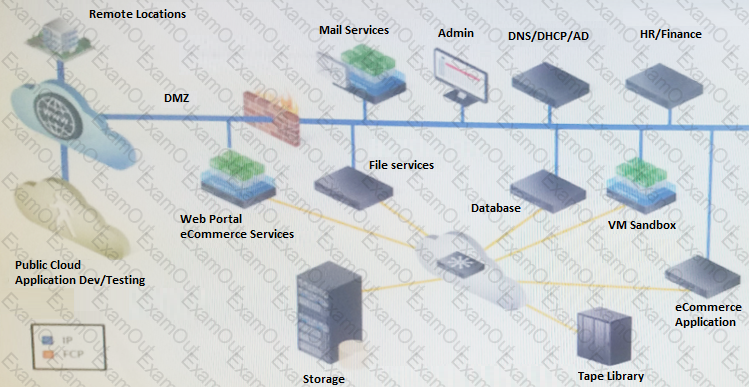
Your company recently negotiated several contracts with new customers to use its proprietary eCommerce system. As a result, the customer base has grown rapidly, which has introduced several challenges and requirements.
Business requirements:
Applications need to scale quickly
Metrics and reporting to anticipate business trends and efficient use of resources
External customers are looking to license the eCommerce application
Other considerations:
Applications need to be recorded for the public cloud
Address security vulnerabilities for customer data in the cloud
Refer to Case 1.
You are designing a transformation from Platform 2.0 to cloud. You review the existing infrastructure and
business requirements. You must define the method to connect the on-premises network directly to the public cloud provider.
Which technology should you select?
An organization is considering the use of a cloud gateway to back up services in their private cloud
environment. They want to use their existing backup application.
What should they ensure about the cloud gateway appliance?
A cloud architect is designing a hybrid cloud for an organization. A requirement for this environment is that the private cloud user credential be trusted by both cloud provisioning APIs.
Which type of authentication will meet this requirement?
What is the key factor used in Business Value Analysis?
SPECIAL INSTRUCTIONS REMINDER
The remaining questions are associated with two cases.
Each case has an introductory, descriptive passage (case text) that describes background information and requirements for a specific cloud based design. And each case has a set of six related, randomized questions. You will need to read the case text in order to answer the related questions correctly.
Given that there are two cases with six scored questions each, the total number of case-based scored questions is 12.
When you display each questions you can easily review the related case text in a pop-up window by clicking on the “Case” icon (shown below)
Case 4
Refer to the exhibit.
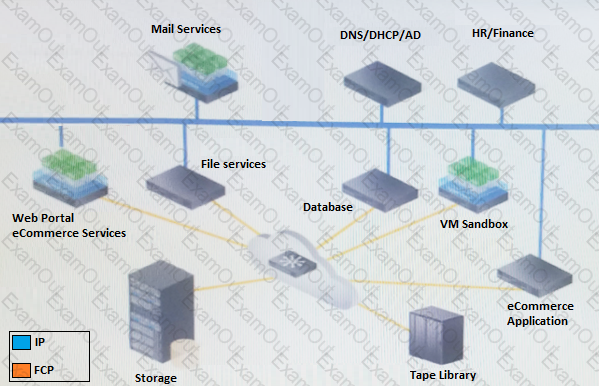
Your company is currently using a traditional SAN storage network. The server infrastructure is partially virtualized. There is a public cloud in place that is used to test development and application migration to cloud.
Business requirements:
Consolidate the network, storage, and compute resources
Simplify network management and storage provisioning
Maintain application performance
Need to share resources to reduce cost and improve efficiency
Other considerations:
Monitoring of protection SLAs
All transactions must be logged for auditing review
Users are validated using internal credentials
Refer to Case 4.
You are designing the network components for a Do-It-Yourself private cloud solution. You want to restrict domain events and minimize traffic disruptions between nodes.
Which compute to storage connectivity solution provides this function?
Which design consideration applies to object storage?

