What is used for migrating data from legacy system volumes to SC default provisioned volumes?
Based on best practices, which configuration represents how an SC9000 storage array with one SC420 expansion enclosure is cabled?
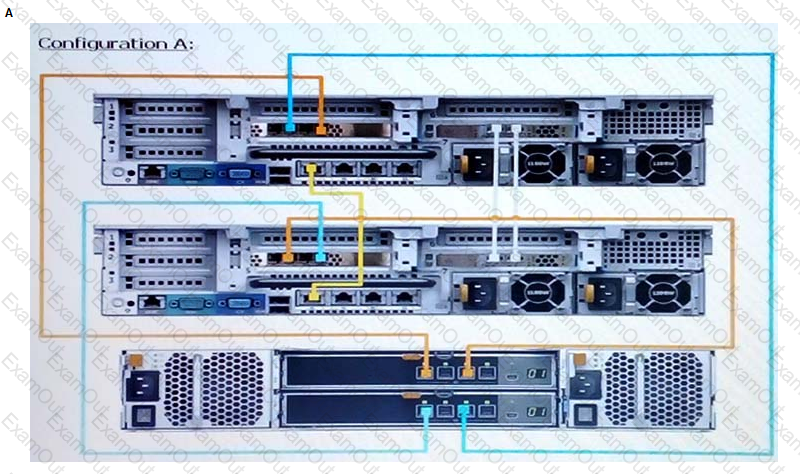
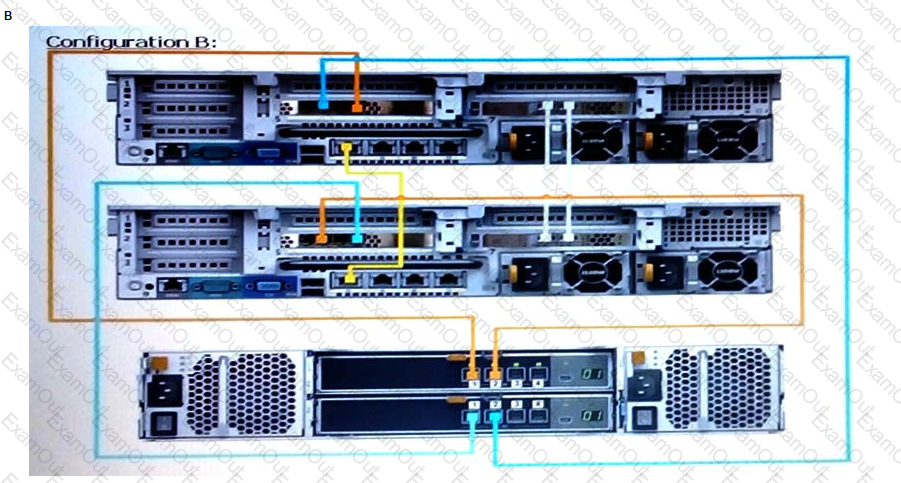
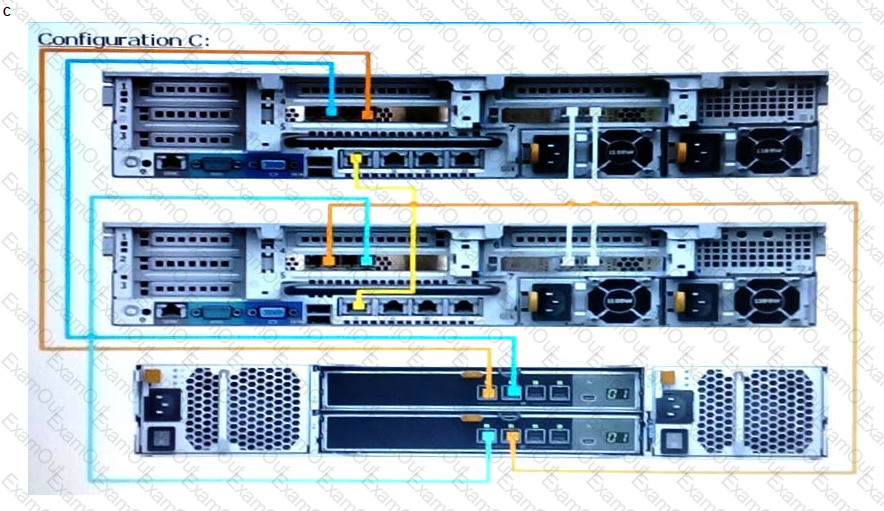
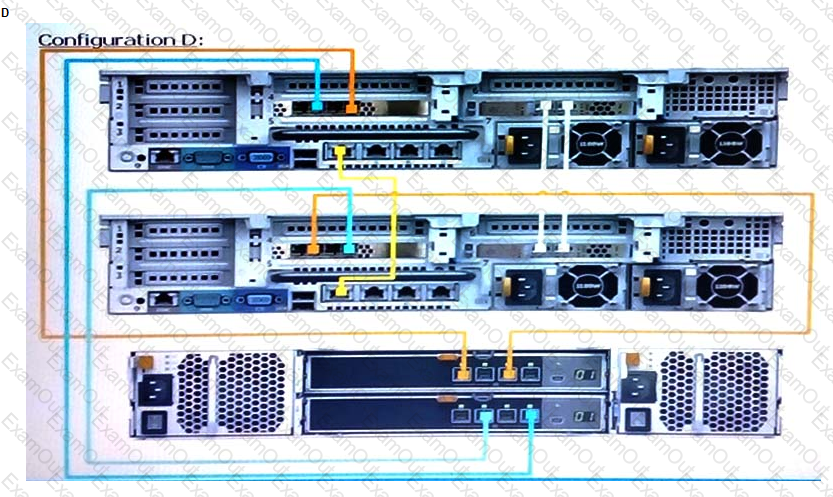
You are installing a new SC9000. Which procedure should be used to install and configure the system?
How many SC220 enclosures can be supported by an SC4020 storage array?
When a SC is in a failover state what will occur in the surviving controller?
A customer wants to add an iSCSI path to a Microsoft Windows Server 2012 R1. The server has an existing Fibre Channel path to an SC7020 array for load balancing and high availability.
Which Windows MPIO policy should be configured to achieve the customer’s requirement?
What is the maximum number of Fault Domains on a SCv3000 Storage Center using SAS front-end?
Refer to the Exhibit.
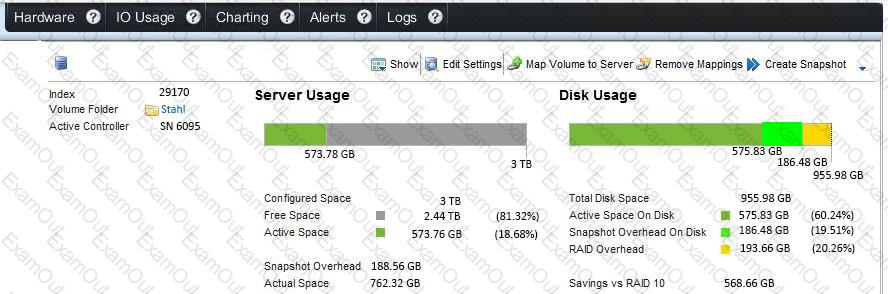
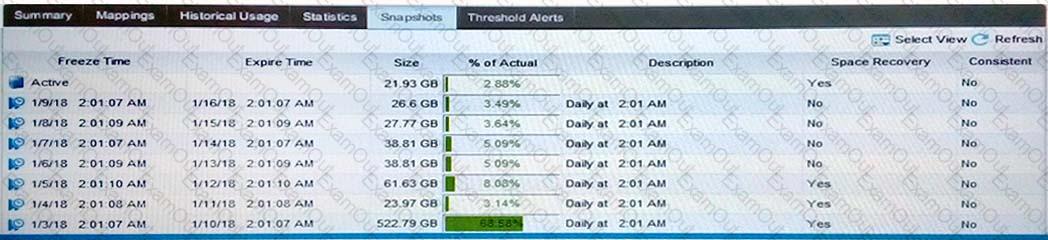
A customer needs your assistance in recovering files that were deleted from an SC Series array volume. The files were deleted around 1:00 AM on January 7th. Based on the exhibit of the Dell Storage Manager (DSM), which recommendation allows the customer to recover the most recent deleted files?
In an SC Series environment, which Fibre Channel zoning method is more secure?
In Storage Manager, what should you do to have the Create Server wizard recognize an HBA properly?

