How many disk drives arc available in a Dell PowerScale F200 node?
An Isilon administrator is receiving “permission denied” while accessing a file on a cluster that an end-user created through an SMB share. The end-user is unable to access the share from their UNIX server.
The end-user “mydomain.com\win_user1” as the login name to access the Microsoft Windows share and then used an LDAP account name of “ux_user1” to access the UNIX mount. The Isilon cluster is joined to the “mydomain.com” Active Directory domain. In additional, the cluster has an LDAP provider attached to it while the on-disk identity is set as “Native”.
What is a possible cause for this permission issue?
A Dell PowerScale cluster has ten A200 nodes and the node pool data protection level is set to N+2. The data access pattern is currently set to streaming If the data access pattern is changed to concurrency, how many stripes for a 1 MB file are moved to other drives?
A company has a 5-node Dell PowerScale cluster on which they want to configure dynamic IP allocation. The pool consists of one. 40 Gbps Ethernet external interface on each of the nodes. Because address space is limited at the company's site, they need to use a minimum number of addresses, evenly allocated across the nodes. The company puts all interfaces in one pool and sets it to dynamic with Round Robin tailover. They need to ensure that, in the case of a node failure, all other nodes take on failover traffic.
How many addresses must be configured on the IP address pool?
Which OneFS 8.0 feature can be added to an NFSv4 export to assist with seamless failover in the event of a disconnect?
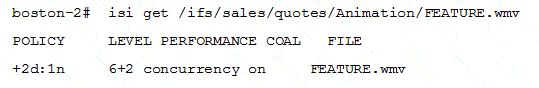
Based on the exhibit, what is the actual protection level of the FEATURE.wmv file?
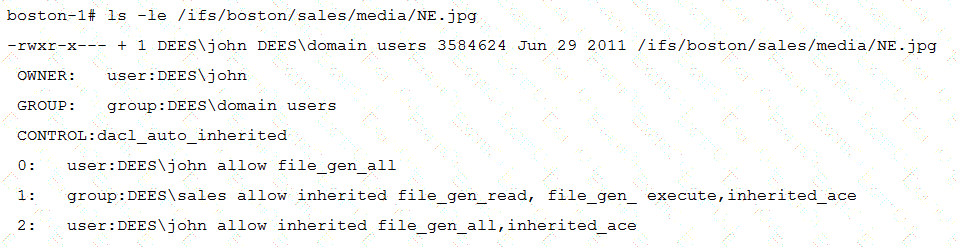
Which access information is represented in the exhibit?
An NFS export is created on a Dell PowerScale cluster. No clients are listed in the export rules What is the result of this condition?
If configuration auditing is enabled, where are the audit logs stored?
A company wants to re-use HD400 nodes into a new cluster with OneFS 8.2.0. What is the minimum number of HD400 nodes required?

