What is true about an OSD storage system?
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
What information is available in a capacity planning report for storage infrastructure?
Which file system provides a streaming interface using the MapReduce framework?
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
What is a benefit of performing local replication?
Which security mechanism ensures secure access to internal assets while enabling Internet-based access to selected resources?
An organization has two data centers separated by a distance of 1600 km. They want to replicate between these data centers for disaster recovery purposes. They are concerned that this will impact application response time.
Which solution will address this concern?
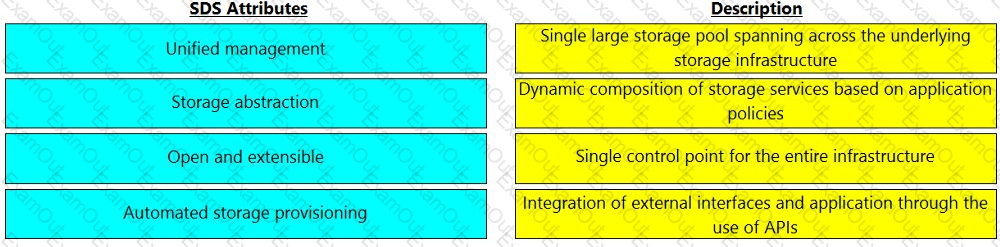
Match the software-defined storage (SDS) attributes with their respective description.