Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client’s operating environment, threat perception, security and compliance requirements, ROE, and budget.
Various components need to be considered for testing while developing the scope of the project.
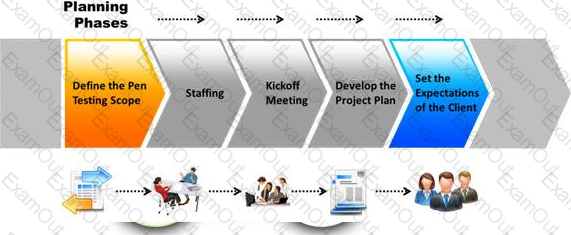
Which of the following is NOT a pen testing component to be tested?
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
Larry is an IT consultant who works for corporations and government agencies. Larry plans on shutting down the city's network using BGP devices and Zombies? What type of Penetration Testing is Larry planning to carry out?
Firewall is an IP packet filter that enforces the filtering and security policies to the flowing network traffic. Using firewalls in IPv6 is still the best way of protection from low level attacks at the network and transport layers.
Which one of the following cannot handle routing protocols properly?
Identify the port numbers used by POP3 and POP3S protocols.
An "idle" system is also referred to as what?
Information gathering is performed to:
i) Collect basic information about the target company and its network
ii) Determine the operating system used, platforms running, web server versions, etc.
iii) Find vulnerabilities and exploits
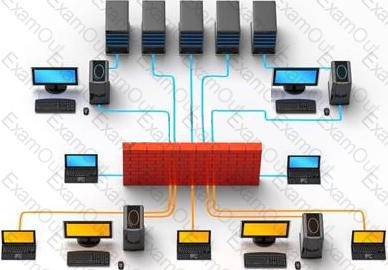
Which of the following pen testing tests yields information about a company’s technology infrastructure?
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?

