Which of the following Trojans would be considered 'Botnet Command Control Center'?
Joseph has just been hired on to a contractor company of the Department of Defense as their Senior Security Analyst. Joseph has been instructed on the company's strict security policies that have been implemented, and the policies that have yet to be put in place. Per the Department of Defense, all DoD users and the users of their contractors must use two-factor authentication to access their networks. Joseph has been delegated the task of researching and implementing the best two-factor authentication method for his company. Joseph's supervisor has told him that they would like to use some type of hardware device in tandem with a security or identifying pin number. Joseph's company has already researched using smart cards and all the resources needed to implement them, but found the smart cards to not be cost effective. What type of device should Joseph use for two-factor authentication?
Attackers send an ACK probe packet with random sequence number, no response means port is filtered (Stateful firewall is present) and RST response means the port is not filtered. What type of Port Scanning is this?
You are the CIO for Avantes Finance International, a global finance company based in Geneva. You are responsible for network functions and logical security throughout the entire corporation. Your company has over 250 servers running Windows Server, 5000 workstations running Windows Vista, and 200 mobile users working from laptops on Windows 7.
Last week, 10 of your company's laptops were stolen from salesmen while at a conference in Amsterdam. These laptops contained proprietary company information. While doing damage assessment on the possible public relations nightmare this may become, a news story leaks about the stolen laptops and also that sensitive information from those computers was posted to a blog online.
What built-in Windows feature could you have implemented to protect the sensitive information on these laptops?
How does a denial-of-service attack work?
Data is sent over the network as clear text (unencrypted) when Basic Authentication is configured on Web Servers.
Study the following exploit code taken from a Linux machine and answer the questions below:
echo “ingreslock stream tcp nowait root /bin/sh sh –I" > /tmp/x;
/usr/sbin/inetd –s /tmp/x;
sleep 10;
/bin/ rm –f /tmp/x AAAA…AAA
In the above exploit code, the command “/bin/sh sh –I" is given.
What is the purpose, and why is ‘sh’ shown twice?
When working with Windows systems, what is the RID of the true administrator account?
A program that defends against a port scanner will attempt to:
What are the differences between SSL and S-HTTP?
An Evil Cracker is attempting to penetrate your private network security. To do this, he must not be seen by your IDS, as it may take action to stop him. What tool might he use to bypass the IDS?
Select the best answer.
When working with Windows systems, what is the RID of the true administrator account?
Which of the following is NOT true of cryptography?
Eve decides to get her hands dirty and tries out a Denial of Service attack that is relatively new to her. This time she envisages using a different kind of method to attack Brownies Inc. Eve tries to forge the packets and uses the broadcast address. She launches an attack similar to that of fraggle. What is the technique that Eve used in the case above?
If you send a SYN to an open port, what is the correct response?(Choose all correct answers.
Rebecca has noted multiple entries in her logs about users attempting to connect on ports that are either not opened or ports that are not for public usage. How can she restrict this type of abuse by limiting access to only specific IP addresses that are trusted by using one of the built-in Linux Operating System tools?
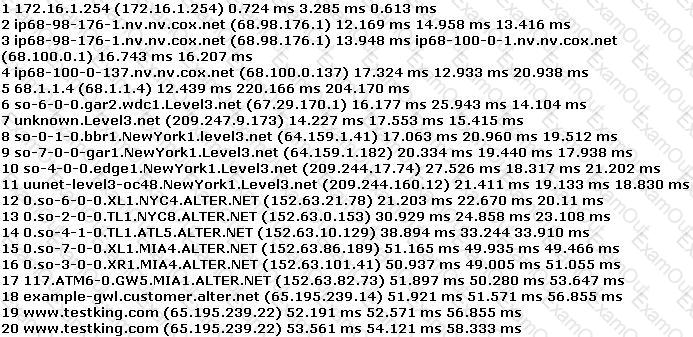
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address.
What can be inferred from this output?
A particular database threat utilizes a SQL injection technique to penetrate a target system. How would an attacker use this technique to compromise a database?
Jim’s organization has just completed a major Linux roll out and now all of the organization’s systems are running the Linux 2.5 kernel. The roll out expenses has posed constraints on purchasing other essential security equipment and software. The organization requires an option to control network traffic and also perform stateful inspection of traffic going into and out of the DMZ.
Which built-in functionality of Linux can achieve this?
Jackson discovers that the wireless AP transmits 128 bytes of plaintext, and the station responds by encrypting the plaintext. It then transmits the resulting ciphertext using the same key and cipher that are used by WEP to encrypt subsequent network traffic. What authentication mechanism is being followed here?

