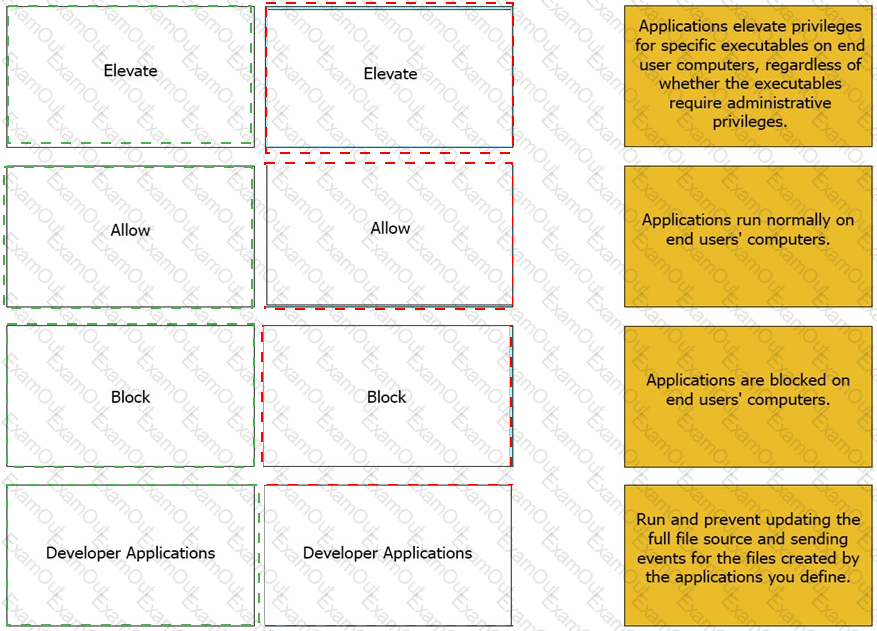
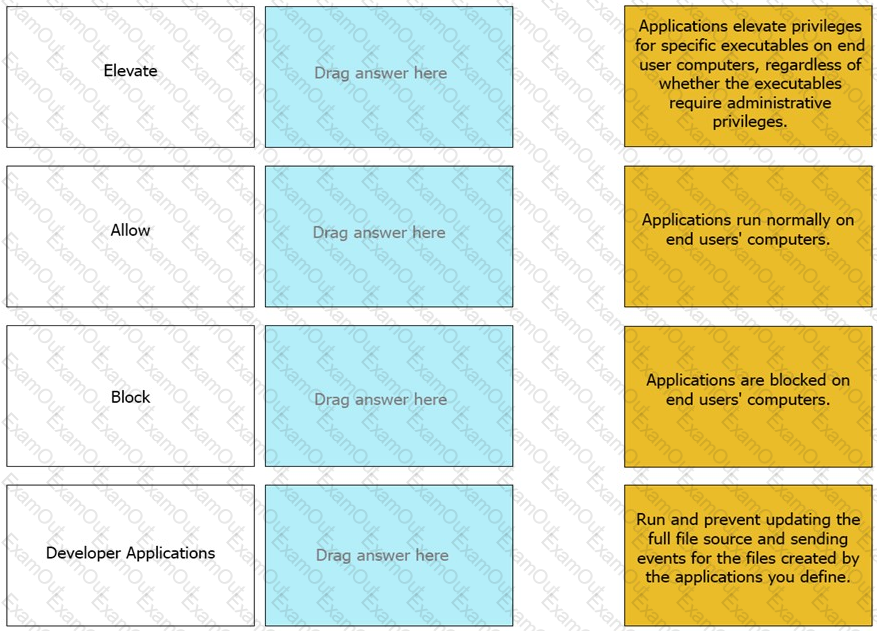
Match the Application Groups policy to their correct description.
If you want to diagnose agent EPM agent connectivity issues, what is the agent executable that can be used from the command line?
When working with credential rotation/loosely connected devices, what additional CyberArk components are required?
An EPM Administrator would like to notify end users whenever the Elevate policy is granting users elevation for their applications. Where should the EPM Administrator go to enable the end-user dialog?
CyberArk's Privilege Threat Protection policies are available for which Operating Systems? (Choose two.)
When blocking applications, what is the recommended practice regarding the end-user UI?
What can you manage by using User Policies?
What type of user can be created from the Threat Deception LSASS Credential Lures feature?
What is required to configure SAML authentication on EPM?
An EPM Administrator would like to include a particular file extension to be monitored and protected under Ransomware Protection. What setting should the EPM Administrator configure to add the extension?