Which of the following is a type of vulnerability that refers to the unauthorized installation of applications on a device through means other than the official application store?
Which of the following is required for an organization to properly manage its restore process in the event of system failure?
Prior to implementing a design change, the change must go through multiple steps to ensure that it does not cause any security issues. Which of the following is most likely to be one of those steps?
The Chief Information Security Officer gives the security community the opportunity to report vulnerabilities on the organization’s public-facing assets. Which of the following does this scenario best describe?
Employees are missing features on company-provided tablets, affecting productivity. Management demands resolution in 48 hours. Which is the best solution?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
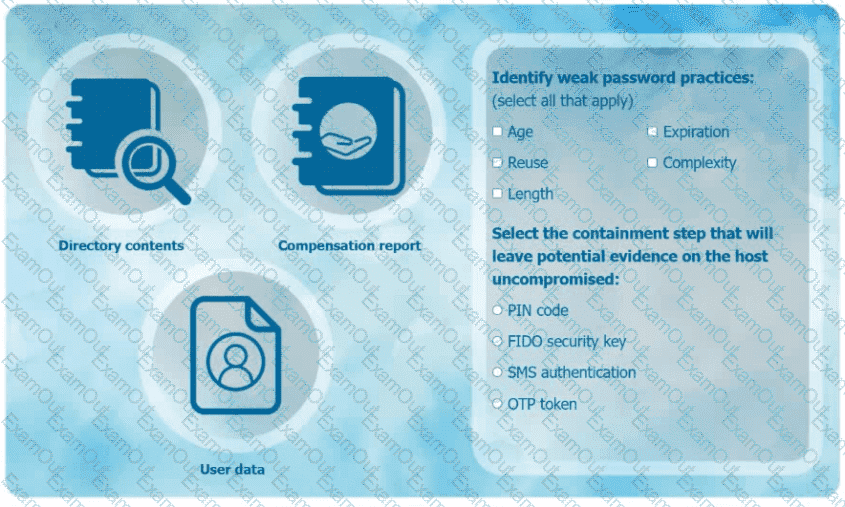
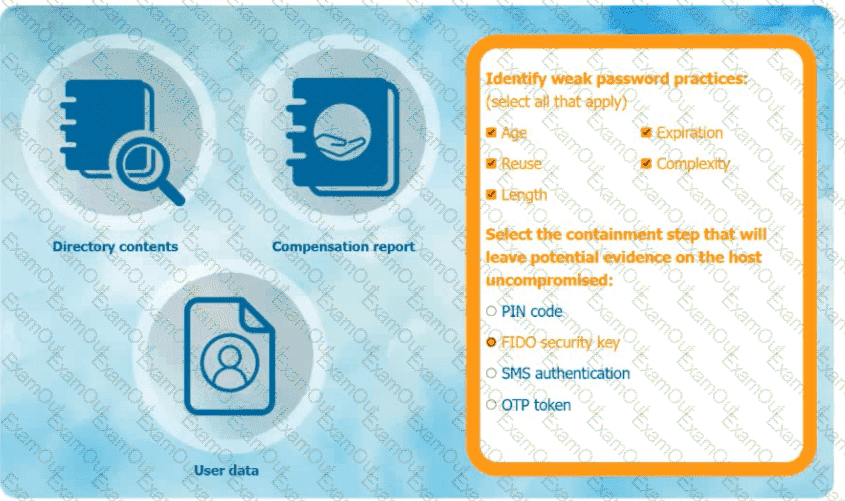
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
Which of the following can be used to mitigate attacks from high-risk regions?
A new employee can select a particular make and model of an employee workstation from a preapproved list. Which of the following is this an example of?
A security engineer is installing an IPS to block signature-based attacks in the environment. Which of the following modes will best accomplish this task?
Which of the following mitigation techniques would a security analyst most likely use to avoid bloatware on devices?
Which of the following should a technician perform to verify the integrity of a file transferred from one device to another?
Which of the following is the final step of the modem response process?
A company is using a legacy FTP server to transfer financial data to a third party. The legacy system does not support SFTP, so a compensating control is needed to protect the sensitive, financial data in transit. Which of the following would be the most appropriate for the company to use?
The analyst wants to move data from production to the UAT server for testing the latest release. Which of the following strategies to protect data should the analyst use?

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.