During an engagement, a penetration tester was able to upload to a server a PHP file with the following content:
Which of the following commands should the penetration tester run to successfully achieve RCE?
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
A penetration tester is conducting an on-path link layer attack in order to take control of a key fob that controls an electric vehicle. Which of the following wireless attacks would allow a penetration tester to achieve a successful attack?
In Java and C/C++, variable initialization is critical because:
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
A penetration testing firm wants to hire three additional consultants to support a newly signed long-term contract with a major customer. The following is a summary of candidate
background checks:
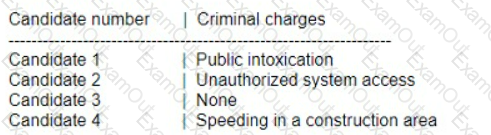
Which of the following candidates should most likely be excluded from consideration?
During a penetration testing engagement, a penetration tester discovers a buffer overflow vulnerability. Which of the following actions should the tester take to maintain professionalism and integrity?
During a REST API security assessment, a penetration tester was able to sniff JSON content containing user credentials. The JSON structure was as follows:
<
transaction_id: "1234S6", content: [ {
user_id: "mrcrowley", password: ["€54321#"] b <
user_id: "ozzy",
password: ["1112228"] ) ]
Assuming that the variable json contains the parsed JSON data, which of the following Python code snippets correctly returns the password for the user ozzy?
A penetration tester gained access to one of the target company's servers. During the enumeration phase, the penetration tester lists the bash history and observes the following row:
Which of the following steps should the penetration tester take next?
A penetration tester wants to crack MD5 hashes more quickly. The tester knows that the first part of the password is Winter followed by four digits and a special character at the end. Which of the following commands should the tester use?

