A database administrator needs to aggregate data from multiple tables in a way that does not impact the original tables, and then provide this information to a department. Which of the following is thebestway for the administrator to accomplish this task?
Which of the following ismostlikely to prevent tampering with server hardware that houses data?
Which of the following is recommended in order to provide encrypted data communication pathways for information as it is transmitted over a network?
Which of the following is used to hide data in a database so the data can only be read by a user who has a key?
Which of the following cloud delivery models provides users with thehighestlevel of flexibility regarding resource provisioning and administration?
An on-premises application server connects to a database in the cloud. Which of the following must be considered to ensure data integrity during transmission?
A database administrator needs to ensure that a newly installed corporate business intelligence application can access the company’s transactional data. Which of the following tasks should the administrator performfirst?
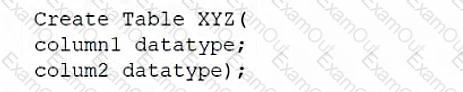
A database administrator would like to create a table named XYZ. Which of the following queries should the database administrator use to create the table?
A)
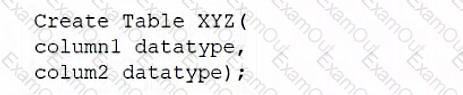
B)
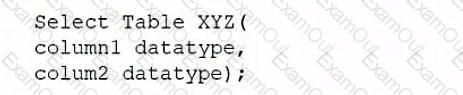
C)
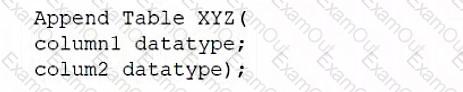
D)
A database administrator set up a connection for a SQL Server instance for a new user, but the administrator is unable to connect using the user's workstation. Which of the following is themostlikely cause of the issue?
Which of the following is part of logical database infrastructure security?

