A network administrator is budding a site-to-site VPN tunnel from the company's headquarters office 10 the company's public cloud development network. The network administrator confirms the following:
The VPN tunnel is established on the headquarter office firewall.
While inside the office, developers report that they cannot connect to the development network resources.
While outside the office on a client VPN, developers report that they can connect to the development network resources.
The office and the client VPN have different IP subnet ranges.
The firewall flow logs show VPN traffic is reaching the development network from the office.
Which of the following is the next step the next network administrator should take to troubleshoot the VPN tunnel?
A cloud engineer needs to determine a scaling approach for a payroll-processing solution that runs on a biweekly basis. Given the complexity of the process, the deployment to each
new VM takes about 25 minutes to get ready. Which of the following would be the best strategy?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
A cloud solution needs to be replaced without interruptions. The replacement process can be completed in phases, but the cost should be kept as low as possible. Which of the
following is the best strategy to implement?
A cloud engineer wants to implement a monitoring solution to detect cryptojacking and other cryptomining malware on cloud instances. Which of the following metrics would most likely be used to identify the activity?
Which of the following types of storage provides the greatest performance advantage for a traditional relational database?
Servers in the hot site are clustered with the main site.
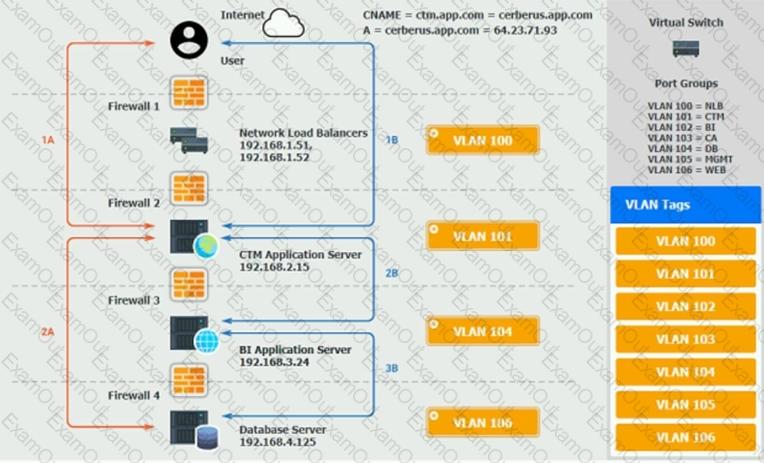
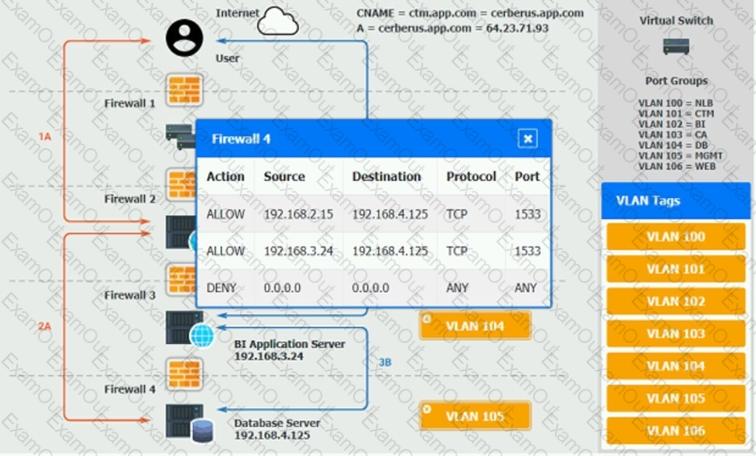
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
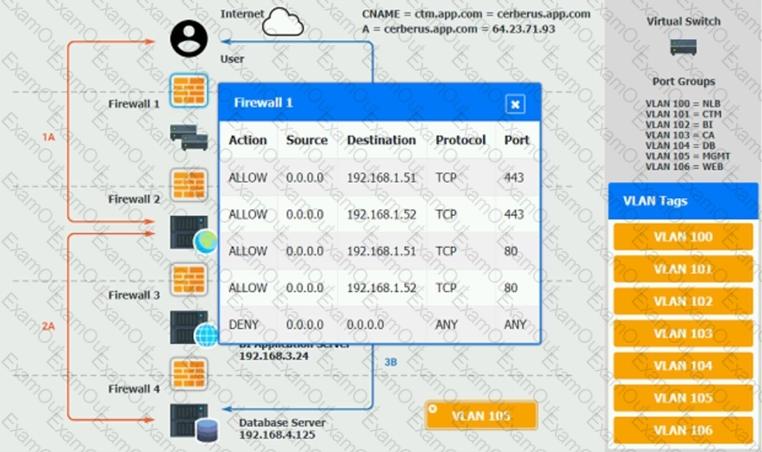
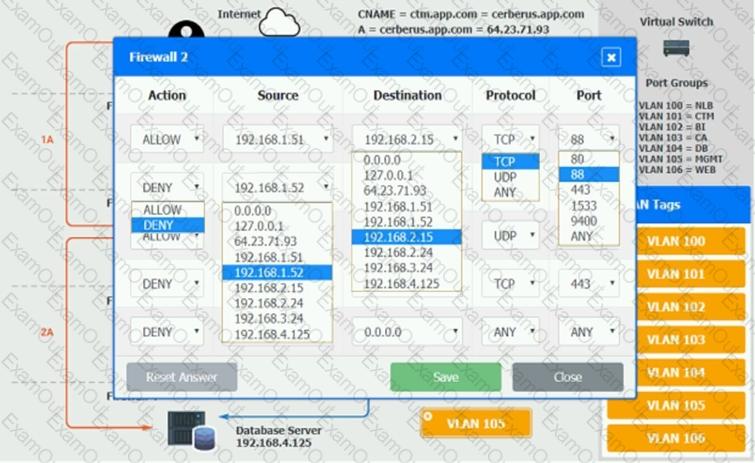
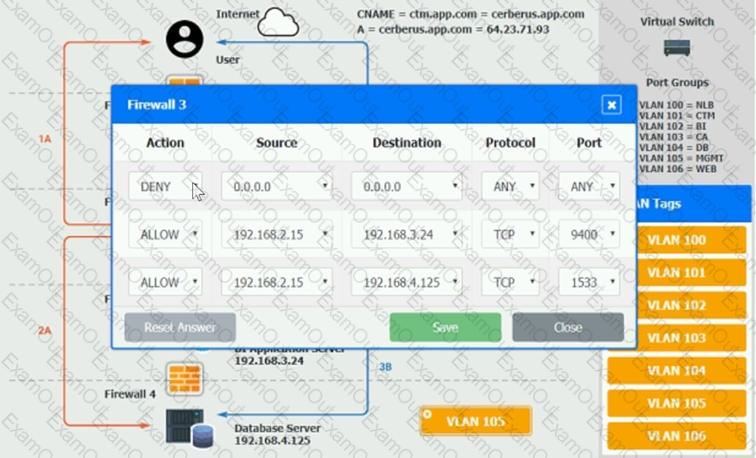
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
During a phase review, two stakeholders discuss the approval of a deliverable. The project manager convinces the stakeholders to agree on a common solution. Which of the following best describes what the project manager did to gain approval from both stakeholders?
A cloud administrator wants to provision a host with two VMs. The VMs require the following:
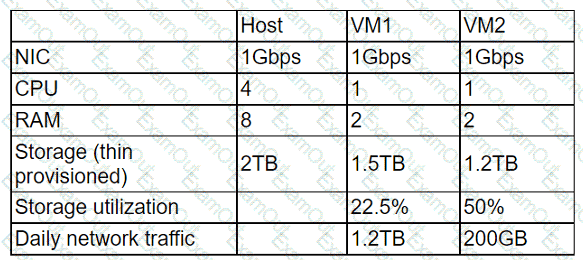
After configuring the servers, the administrator notices that during certain hours of the day, the performance heavily degrades. Which of the following is the best explanation?

