An analyst needs to understand how an attacker compromised a server. Which of the following procedures will best deliver the information that is necessary to reconstruct the steps taken by the attacker?
An incident response team is responding to a breach of multiple systems that contain Pll and PHI Disclosure of the incident to external entities should be based on:
A social media company is planning an acquisition. Prior to the purchase, the Chief Security Officer (CSO) would like a full report to gain a better understanding of the prospective company's cybersecurity posture and to identify risks in the supply chain. Which of the following will best support the CSO's objective?
Which of the following is the primary reason financial institutions may share up-to-date threat intelligence information on a secure feed that is
dedicated to their sector?
A Chief Executive Officer (CEO) is concerned about the company’s intellectual property being leaked to competitors. The security team performed an extensive review but did not find any indication of an outside breach. The data sets are currently encrypted using the Triple Data Encryption Algorithm. Which of the following courses of action is appropriate?
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:

Which of the following ports should be closed?
A forensic examiner is investigating possible malware compromise on an active endpoint device. Which of the following steps should the examiner perform first?
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
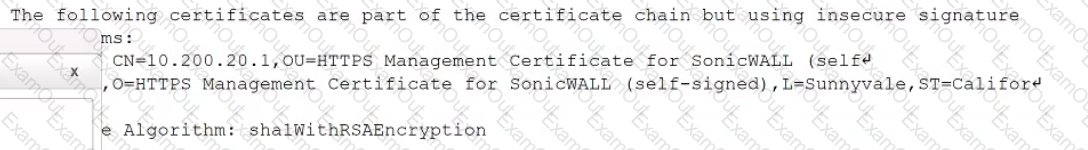 this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
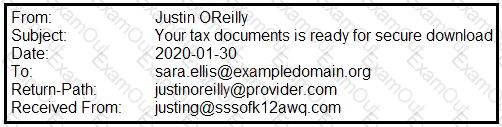
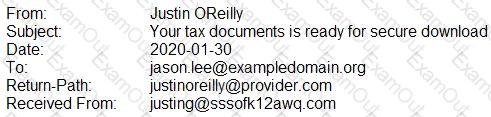
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
A user receives a potentially malicious attachment that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review. Which of the following commands would most likely indicate if the email is malicious?

