An organization is developing software to match customers' expectations. Before the software goes into production, it must meet the following quality assurance guidelines
• Uncover all the software vulnerabilities.
• Safeguard the interest of the software's end users.
• Reduce the likelihood that a defective program will enter production.
• Preserve the Interests of me software producer
Which of me following should be performed FIRST?
Which of the following is the most important reason to involve the human resources department in incident response?
Which of following allows Secure Boot to be enabled?
During routine monitoring a security analyst identified the following enterpnse network traffic:
Packet capture output:
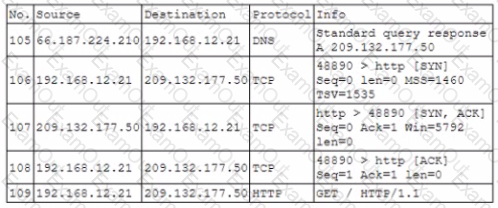
Which of the following BEST describes what the security analyst observed?
An online gaming company was impacted by a ransomware attack. An employee opened an attachment that was received via an SMS attack on a company-issue firewall. Which following actions would help during the forensic analysis of the mobile device? (Select TWO).
A company's legal department is concerned that its incident response plan does not cover the countless ways security incidents can occur. The department has asked a security analyst to help tailor the response plan to provide broad coverage for many situations. Which of the following is the best way to achieve this goal?
While conducting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
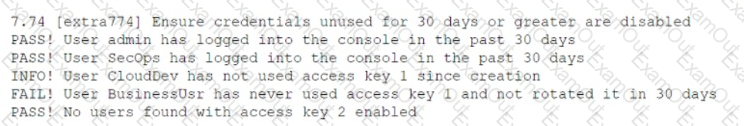
Based on the Prowler report, which of the following is the BEST recommendation?
A company has alerted planning the implemented a vulnerability management procedure. However, to security maturity level is low, so there are some prerequisites to complete before risk calculation and prioritization. Which of the following should be completed FIRST?
Which of the following types of controls defines placing an ACL on a file folder?
Which of the following is the best method to ensure secure boot UEFI features are enabled to prevent boot malware?

