A financial organization has offices located globally. Per the organization’s policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's data. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations to help mitigate this risk. The Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
At which of the following phases of the SDLC shoukJ security FIRST be involved?
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A cybersecunty analyst needs to harden a server that is currently being used as a web server The server needs to be accessible when entenng www company com into the browser Additionally web pages require frequent updates which are performed by a remote contractor Given the following output:
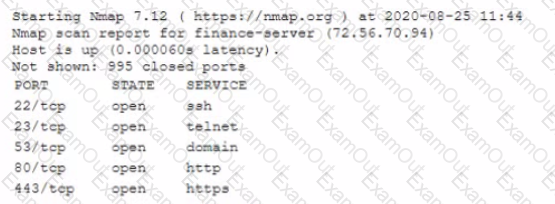
Which of the following should the cybersecunty analyst recommend to harden the server? (Select TWO).
An organization is performing a risk assessment to prioritize resources for mitigation and remediation based on impact. Which of the following metrics, in addition to the CVSS for each CVE, would best enable the organization to prioritize its efforts?
During a forensic investigation, a security analyst reviews some Session Initiation Protocol packets that came from a suspicious IP address. Law enforcement requires access to a VoIP call
that originated from the suspicious IP address. Which of the following should the analyst use to accomplish this task?
The following output is from a tcpdump al the edge of the corporate network:
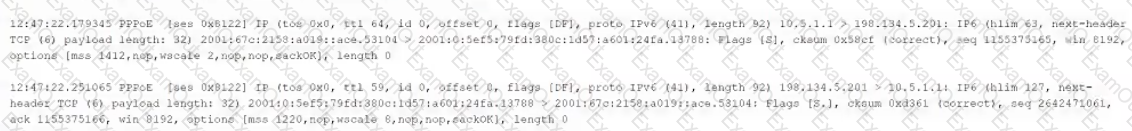
Which of the following best describes the potential security concern?
A security manager has asked an analyst to provide feedback on the results of a penetration test. After reviewing the results, the manager requests
information regarding the possible exploitation of vulnerabilities. Which of the following information data points would be MOST useful for the analyst
to provide to the security manager, who would then communicate the risk factors to the senior management team? (Select TWO).
Which of the following is a reason to use a nsk-based cybersecunty framework?

