A company's Chief Information Officer wants to use a CASB solution to ensure policies are being met during cloud access. Due to the nature of the company's business and risk appetite, the management team elected to not store financial information in the cloud. A security analyst needs to recommend a solution to mitigate the threat of financial data leakage into the cloud. Which of the following should the analyst recommend?
An incident response team detected malicious software that could have gained access to credit card data. The incident response team was able to mitigate significant damage and implement corrective actions. By having incident response mechanisms in place. Which of the following should be notified for lessons learned?
Which of the following organizational initiatives would be MOST impacted by data severighty issues?
The security team decides to meet informally to discuss and test the response plan for potential security breaches and emergency situations. Which of the following types of training will the security team perform?
A security analyst is reviewing the following Internet usage trend report:
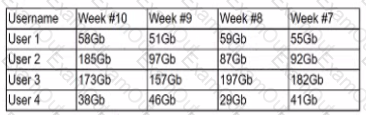
Which of the following usernames should the security analyst investigate further?
Which of the following is MOST dangerous to the client environment during a vulnerability assessment penetration test?
Company A is m the process of merging with Company B As part of the merger, connectivity between the ERP systems must be established so portent financial information can be shared between the two entitles. Which of the following will establish a more automated approach to secure data transfers between the two entities?
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further in investigation?
Which of the following is an advantage of continuous monitoring as a way to help protect an enterprise?
During a review of the vulnerability scan results on a server, an information security analyst notices the following:
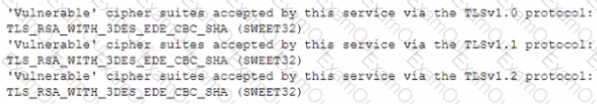
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:

