Scenario: A Citrix Architect needs to assess an existing NetScaler multi-site deployment. The deployment is using Global Server Load Balancing (GSLB) configured in a parent-child configuration.
Click the Exhibit button to view the diagram of the current GSLB configuration and parent-child relationships, as well as the status of the sites and the connectivity between them.
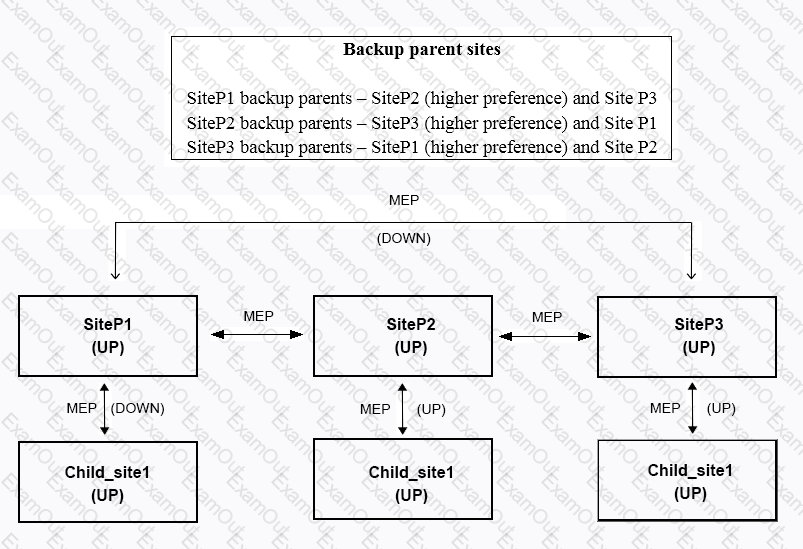
Based on the displayed configuration and status, Child_site1_______ a connection from _______. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to deploy a load balancing for an application server on the NetScaler. The authentication must be performed on the NetScaler. After the authentication, the Single Sign-on with the application servers must be performed using Kerberos impersonation.
Which three authentication methods can the Architect utilize to gather the credentials from the user in this scenario? (Choose three.)
Which two methods can a Citrix Architect use to create a Heat Orchestration template? (Choose two)
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:
IP address reputation
HTML SQL injection check
Start URL
HTML Cross-site scripting
Form-field consistency
After deployment in pre-production, the team identifies the following additional security features and changes as further requirements:
Application Firewall should retain the response of form field in its memory When a client submits the form in the next request. Application Firewall should check for inconsistency in the request before sending it to the web server
All the requests dropped by Application Firewall should receive a pre-configured HTML error page with appropriate information.
The Application Firewall profile should be able to handle the data from the RSS feed and an ATOM-based site.
Click the Exhibit button to view an excerpt of the existing configuration.
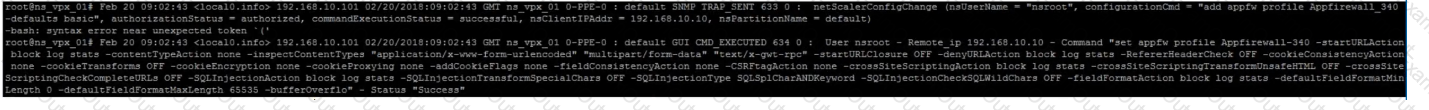
What should the architect do to meet these requirements?
Scenario: A Citrix Architect needs to configure a Content Switching virtual server to provide access to www.workspacelab.com . However, the architect observes that whenever the user tries to access www.worksapcelab.com/CITRIX/WEB , the user receives a "503 - Service Unavailable" response. The configuration snippet is as follows:
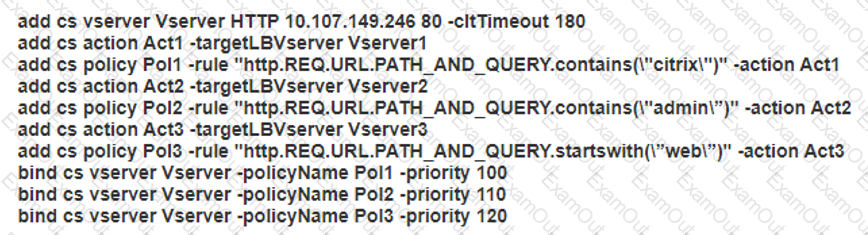
What should the architect modify to resolve this issue?
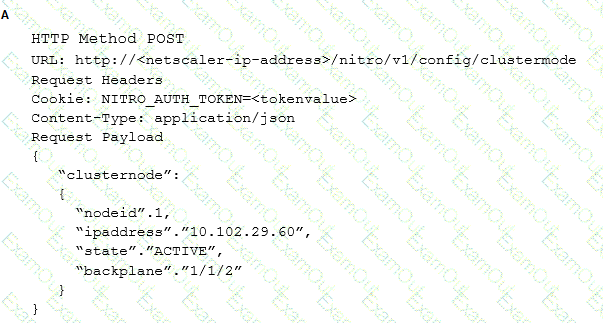
Which request can a Citrix Architect utilize to create a NITRO API command to add a NetScaler appliance with NSIP address 10.102.29.60 to the cluster?
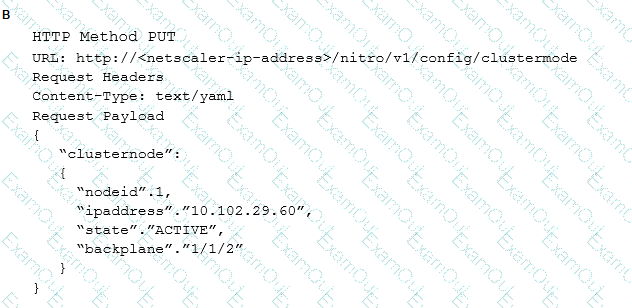
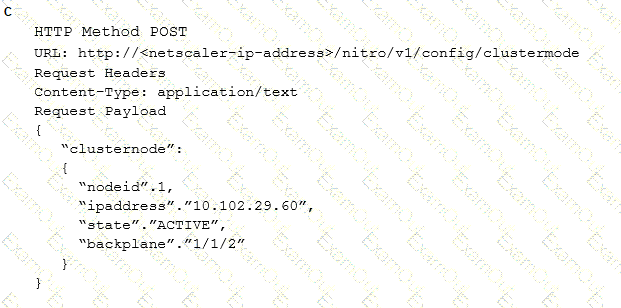
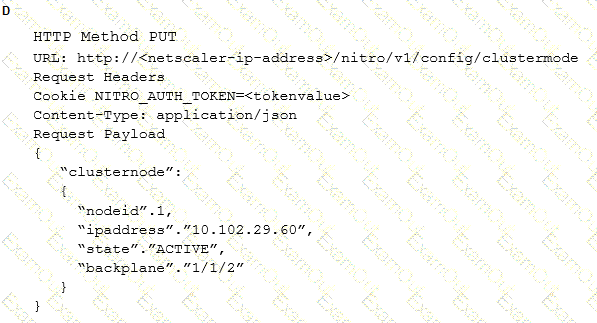
Scenario: A Citrix Architect is asked by management at the Workspacelab organization to review their existing configuration and make the necessary upgrades. The architect recommends small changes to the pre-existing Citrix ADC configuration. Currently, the Citrix ADC MPX devices are configured in a high availability pair, and the outbound traffic is load balanced between two Internet service providers (ISPs). However, the failover is NOT happening correctly. The following requirements were discussed during the design requirement phase:
• The return traffic for a specific flow should be routed through the same path while using Link Load Balancing.
• The link should fail over even if the ISP router is up and intermediary devices to an ISP router are down.
• Traffic going through one ISP router should fail over to the secondary ISP, and the traffic should NOT flow through both routers simultaneously. What should the architect configure to meet this requirement?
Scenario: A Citrix Architect has deployed two MPX devices. 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm and the devices are installed behind a CISCO ASA 5585 Firewall. The architect enabled the following features on the Citrix ADC devices. Content Switching. SSL Offloading, Load Balancing, Citrix Gateway. Application Firewall in hybrid security and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration.
All traffic should be secured and any traffic coming Into FITTP should be redirected to HTTPS.
Single Sign-on should be created for Microsoft Outlook web access (OWA).
Citrix ADC should recognize Uniform Resource Identifier (URI) and close the session to Citrix ADC when users hit the Logoff button In Microsoft Outlook web access.
Users should be able to authenticate using either user principal name (UPN) or sAMAccountName.
The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers and the monitor probes must be sent on SSL.
Which monitor will meet these requirements?
Scenario: A Citrix Architect needs to design a hybrid Citrix Virtual App and Citrix Virtual Desktop environment which will include as well as resource locations in an on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
Active Citrix Virtual App and Citrix Virtual Desktop Service subscription
No existing Citrix deployment
Minimization of additional costs
All users should correct directly to the resource locations containing the servers which will host HDX sessions
Click the Exhibit button to view the conceptual environment architecture.
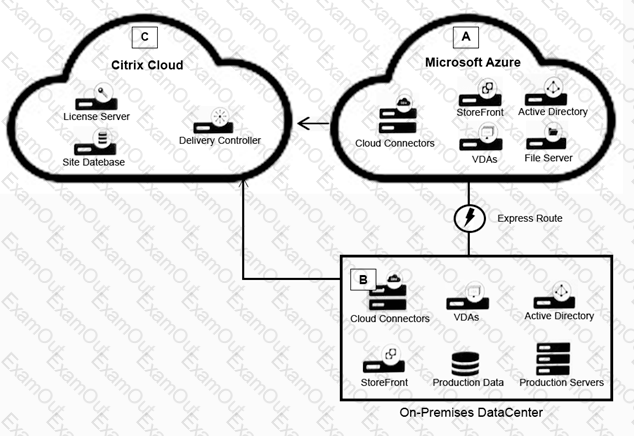
The architect should use___________ in Location A, and should use _______________ in Location B. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect needs to design a new Citrix Gateway deployment for a customer. During the design discussions, the architect documents the key
requirements for the Citrix Gateway.
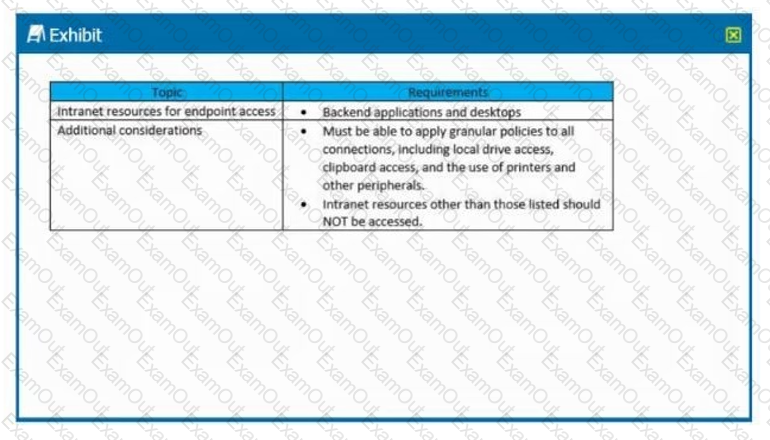
Click the Exhibit button to view the key requirements.
The architect should configure Citrix Gateway for __________________in order to meet the stated requirements. (Choose the correct option to complete the
sentence.)

