Which CiscoSecurity benefit is a differentiator that allows partners to plan and model their business?
Refer to the exhibit.
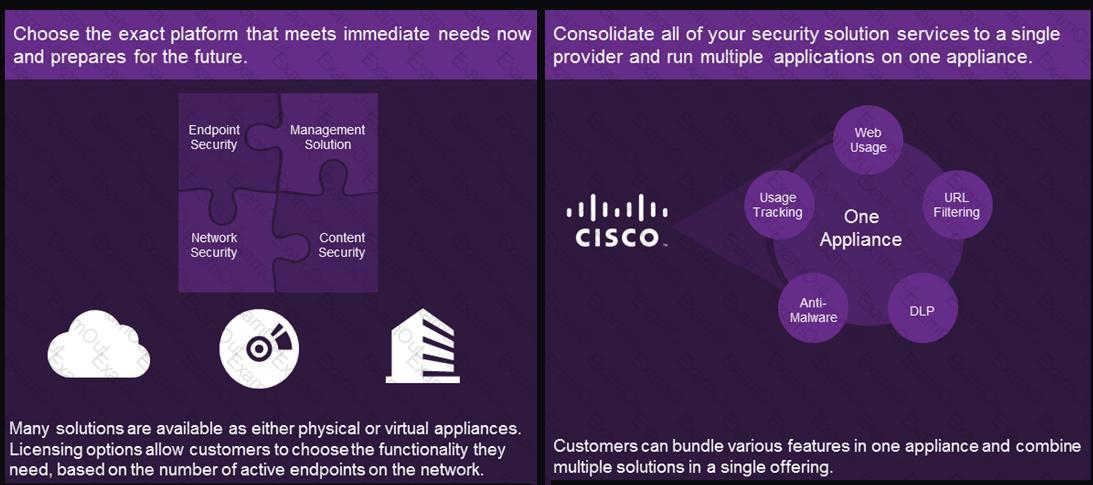
Consolidating platforms and appliances under a single provider is an example of which customer cost saver?
Which three options are a result of utilizing a fragmented security model? (Choose three.)
Which component of NGFW and NGIPS provides a unified image that includes the Cisco ASA features and FirePOWER Services?
Which two attack vectors are protected by malware protection? (Choose (two.)
Which component of AMP provides the details that customers need to address problems after a breach is identified?
Which Cisco security technology delivers the best real-time threat intelligence?
Which three options does Cisco provide to customers for complete protection against current secunty threats? (Choose three )
Which three security vectors must customers monitor to overcome security challenges? (Choose three.)
Which customer cost saver leverages current infrastructures without buying new appliances and avoids lengthy customizations?

