An engineer needs to install a new package on a Cisco Nexus 9000 Series Switch. What is the impact of running the install commit
All logins to a Cisco Nexus 9000 Series Switch must pass through the TACACS+ server at IP address 192.168.10.10. The configuration must meet these requirements:
• The TACACS+ server must be used for SSH and Telnet.
• The TACACS+ server key must be Cisco123!.
• Management VRF must be used for connectivity.
• The deployment must fail back to local credentials if the TACACS+ server fails to respond within 30 seconds.
Drag and drop the code snippets from the right onto the blanks in the code on the left to complete the configuration. Not all code snippets are used.

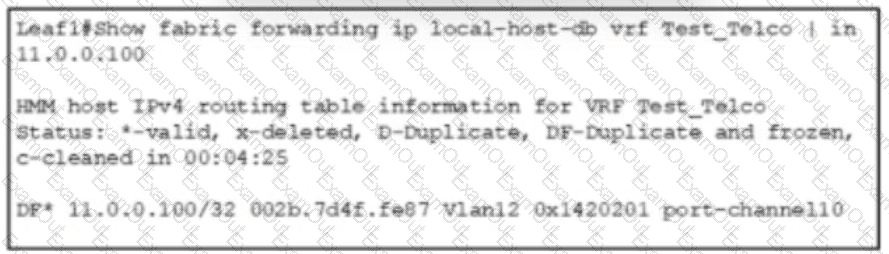
Refer to the exhibit A Cisco VXLAN fabric must detect when a VM with an IP address of 11.0.0.100 moves between servers The engineer must also unfreeze the endpoint Which command accomplishes this goal?
An engineer must replace a defective fabric interconnect with the same model. The system must be restored, including the database of locally created users. The equivalent Cisco UCS Manager software version must be used. Which backup type must be used to meet these requirements?
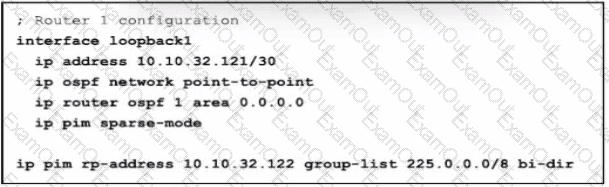
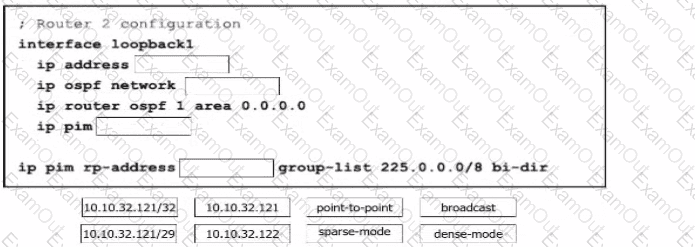
Refer to the exhibit. In a bidirectional PIM network using Phantom RP as an RP redundancy mechanism, two Cisco NX-OS routers have these requirements:
•R1 must be the active RP.
•R2 must be the backup RP that is used only if R1 is not reachable
Drag and drop the configuration steps to complete the configuration for Router 2 Not all configuration steps are used.
An engineer must perform a nondisruptive software upgrade on a dual supervisor Cisco Nexus 7000 series switch. What is the cause of the upgrade being disruptive?
What is the impact of a nondisruptive upgrade on fabric and modular switches?
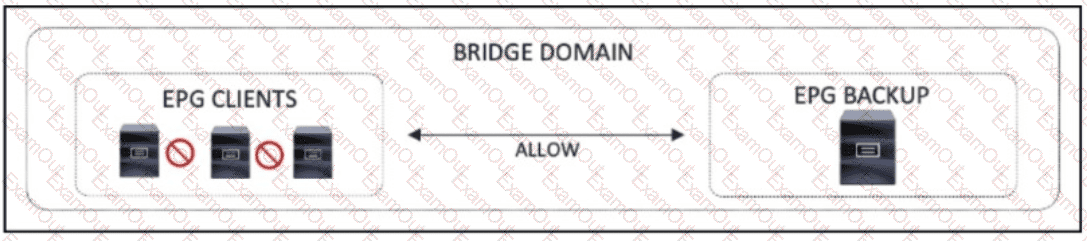
Refer to the exhibit. A network engineer must implement a micro-segmentation solution to allow communication between client and server EPGs but restrict traffic between endpoints located on the same EPG In the current deployment, all EPGs are members of the preferred group Which configuration meets these requirements?
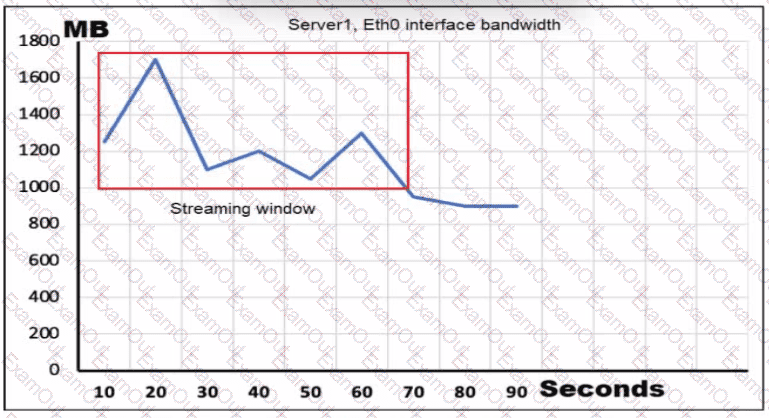
Refer to the exhibit. Server1 is connected to a Cisco Nexus 9000 Series Switch via a 1-Gb pod channel. The storm control is applied to the Eth0 device with a zero percent value What does the switch do to traffic that traverses the switch interfaces during the streaming window that exceeds the bandwidth of the interfaces?
A Cisco UCS user called "Employee1" accidentally changed the boot policy of the Cisco UCS server at the Cisco UCS Manager root level. This change impacted all service profiles and their storage connectivity was lost. The system administrator wants to prevent this issue from recurring in the future. The new security policy mandates that access must be restricted up to the organization level and prevent other users from modifying root policies. Which action must be taken to meet these requirements?



