A user misplaces a personal phone and wants to blacklist the device from accessing the company network. The company uses Cisco ISE for corporate and BYOD device authentication. Which action must the user take in Cisco ISE?
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
What does the dot1x system-auth-control command do?
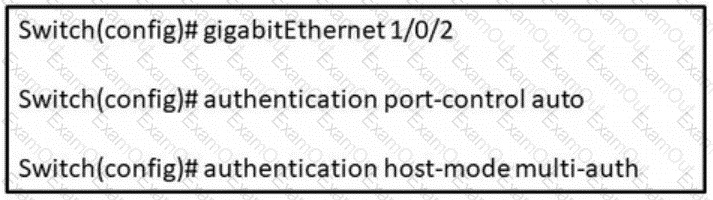
Refer to the exhibit. In which scenario does this switch configuration apply?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
An organization wants to split their Cisco ISE deployment to separate the device administration functionalities from the mam deployment. For this to work, the administrator must deregister any nodes that will become a part of the new deployment, but the button for this option is grayed out Which configuration is causing this behavior?
Which two Cisco ISE deployment models require two nodes configured with dedicated PAN and MnT personas? (Choose two.)
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
A network administrator changed a Cisco ISE deployment from pilot to production and noticed that the JVM memory utilization increased significantly. The administrator suspects this is due to replication between the nodes What must be configured to minimize performance degradation?

