Leaf 1002 receives a packet from a host attached to Leaf1001. The packet contains the MAC address. IP address, and VRF of the source. Which information does each node learn?
An engineer Is configuring a Cisco ACI fabric and requires a shared L30ut network connectivity to external networks. The connectivity must be shared between different tenants. Which tenant type must be created to meet this requirement?
An engineer designs a Cisco ACI Multi-Pod solution that requires a pair of active-standby firewalls in different pods for external connectivity. How should the firewalls be implemented?
Cisco ACI fabric is migrated from network-centric mode to application-centric mode. What is possible in an application-centric design?
What is the advantage of implementing an active-active firewall cluster that is stretched across separate pods when anycast services are configured?
Refer to the exhibit.
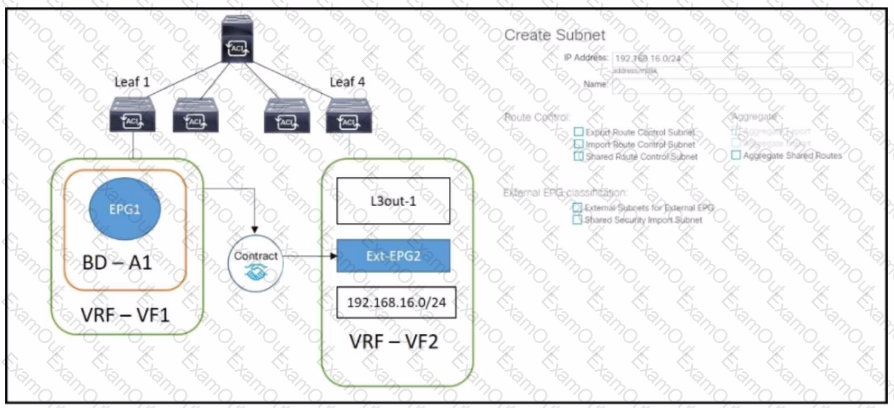
The external subnet and internal EPG1 must communicate with each other, and the L30ut traffic must leak Into the VRF named "VF1". Which configuration set accomplishes these goals?
An organization deploys active-active data centers and active-standby firewalls in each data center. Which action should be taken in a Cisco ACI Multi-Pod to maintain traffic symmetry through the firewalls?
Refer to the exhibit.
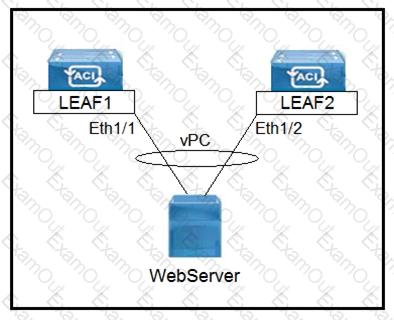
Which three actions should be taken to implement the vPC in the Cisco ACI fabric? (Choose three.)
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
A network engineer configured an active-active firewall cluster that is stretched across separate pods in the Cisco ACI fabric. Which two implementation setups for anycast services are available? (Choose two.)

