What are two security benefits of a Docker-based application?
What should a CI/CD pipeline aim to achieve?
Package updates from a local server fail to download. However, the same updates work when a much slower external repository is used. Way are local updates failing?
Which product provides network controller-level management features?
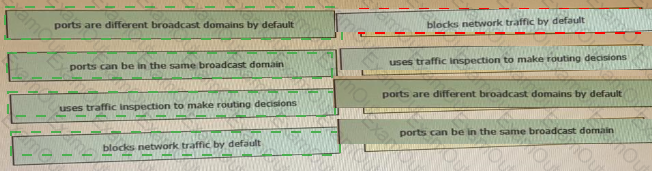
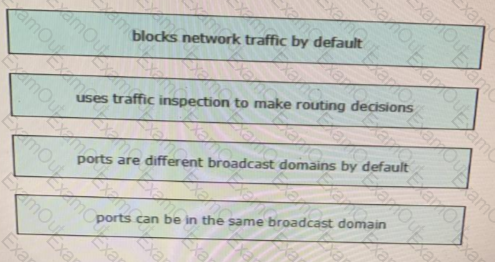
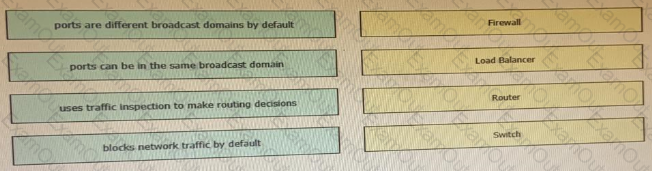
Drag and drop the functionalities from the left onto correct networking devices on the right.
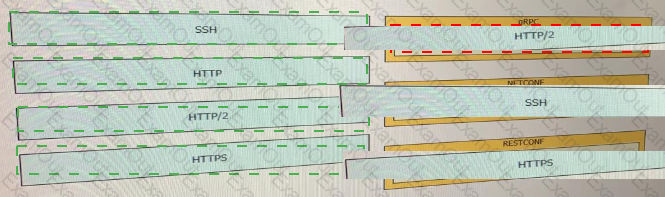
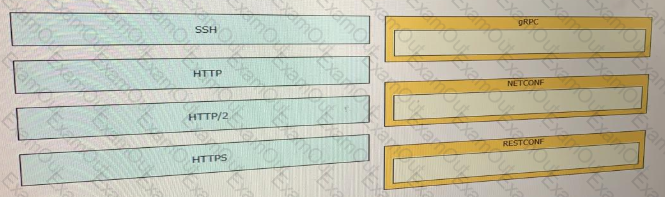
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. (Not all Options are used)
Which two encoding formats do YANG interfaces support?
A 401 HTTP response code is returned when calling a REST API. What is the error state identified by this response code?
On which port does NETCONF operate by default?
Refer to the exhibit.
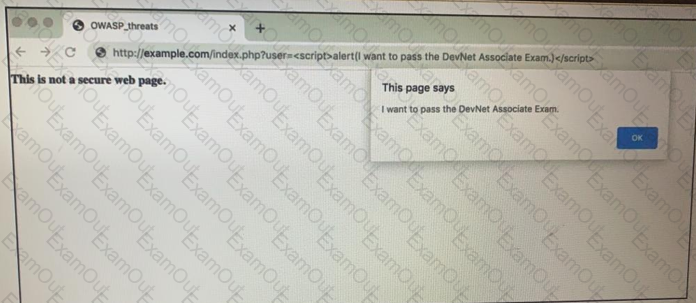
Which OWASP threat does this example demonstrate?