Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
What are two properties of private IP addresses? (Choose two.)
Refer to the exhibit.
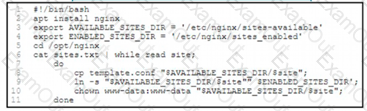
An engineer must configure a load balancer server. The engineer prepares a script to automate workflow by using Bash. The script install the nginx package, moves to the /optAtginx directory, and reads the sites M We (or further processing Based on the script workflow, which process is being automated within the loop by using the information mi sites txt?
Refer to the exhibit.
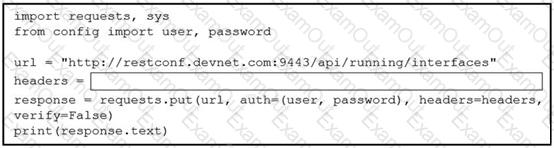
A network engineer wants to use an API to update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which line of code needs to be placed in the snippet where the code is missing?
A company is adopting DevOps as part of an internal transformation, and is reviewing the success of the first deployments. Developers and engineers are working together to resolve any resulting issues. However, this new way of working has increased overhead, and the team is finding it difficult to complete releases in time.
Which area of the CALMS framework must the company target for improvement?
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as “latest”. Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
Refer to the exhibit.

A developer must integrate a bot with an internal communication app. The developer wants to replace the webexbot package with the teamsbot package by using Ansible and prepares a playbook In the first two tasks, the playbook stops the webexbot and verifies that the teamsbot is installed. What is accomplished in the last task of the workflow when the developer runs the Ansible playbook?
While developing a real-Time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
What is the function of IP address in networking?

