Which model-driven programmability protocol does Cisco IOS XE Software support?
When using the Bash shell, how it the output of the devnet command saved to a tile named “output.txt”?
How does requesting a synchronous API operation differ from requesting an asynchronous API operation?
what is an advantage of a version control system?
Refer to the exhibit.
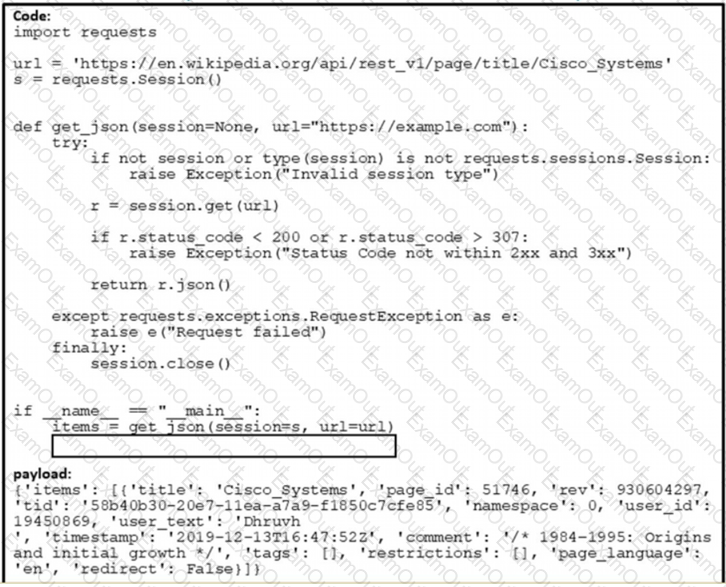
Which command needs to be placed on the box where the code is missing to output the value of page_jd in the Python 3.7 script?
A)

B)

C)

D)

Refer to the exhibit.
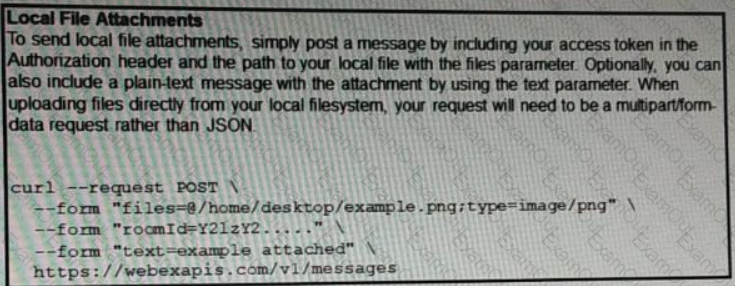
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
Refer to the exhibit.
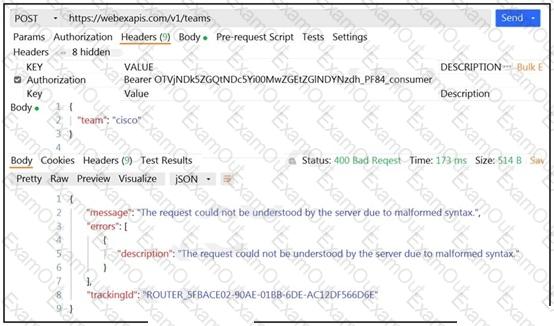
A developer wants to create a room named cisco through Webex API. The developer prepares the request by putting an API token inside the authorization header; however, the given HTTP call returns error code 400. How must the call parameters be changed to ensure a valid response?
How are load balancers used in modern application deployment?
Refer to the exhibit.
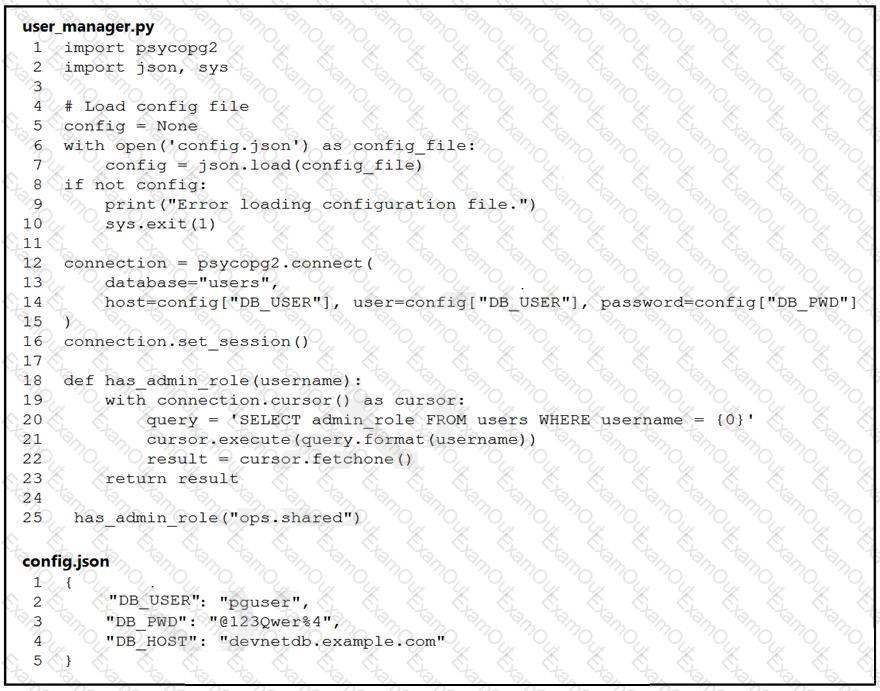
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
Refer to the exhibit.
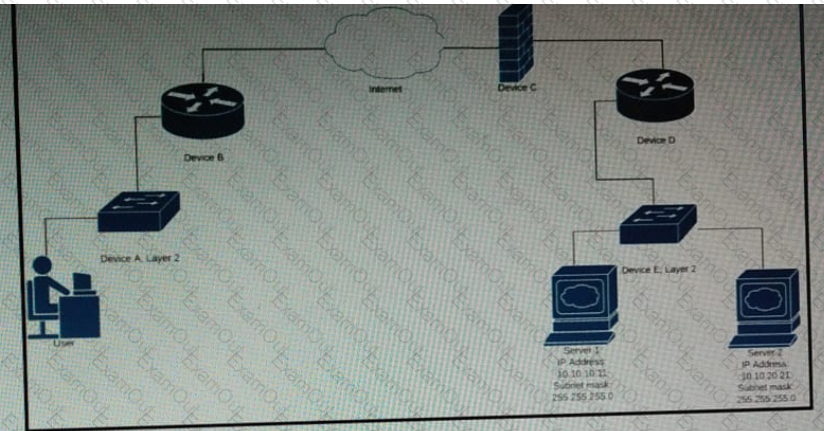
Which device limits traffic between server 1 and server 2?

