Which Check Point software blade provides Application Security and identity control?
You notice that your firewall is under a DDoS attack and would like to enable the Penalty Box feature, which command you use?
What mechanism can ensure that the Security Gateway can communicate with the Management Server with ease in situations with overwhelmed network resources?
Which of the following is NOT a component of a Distinguished Name?
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the tight protections in place. Check Point has been selected for the security vendor.
Which Check Point product protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
The “MAC magic” value must be modified under the following condition:
On the following picture an administrator configures Identity Awareness:
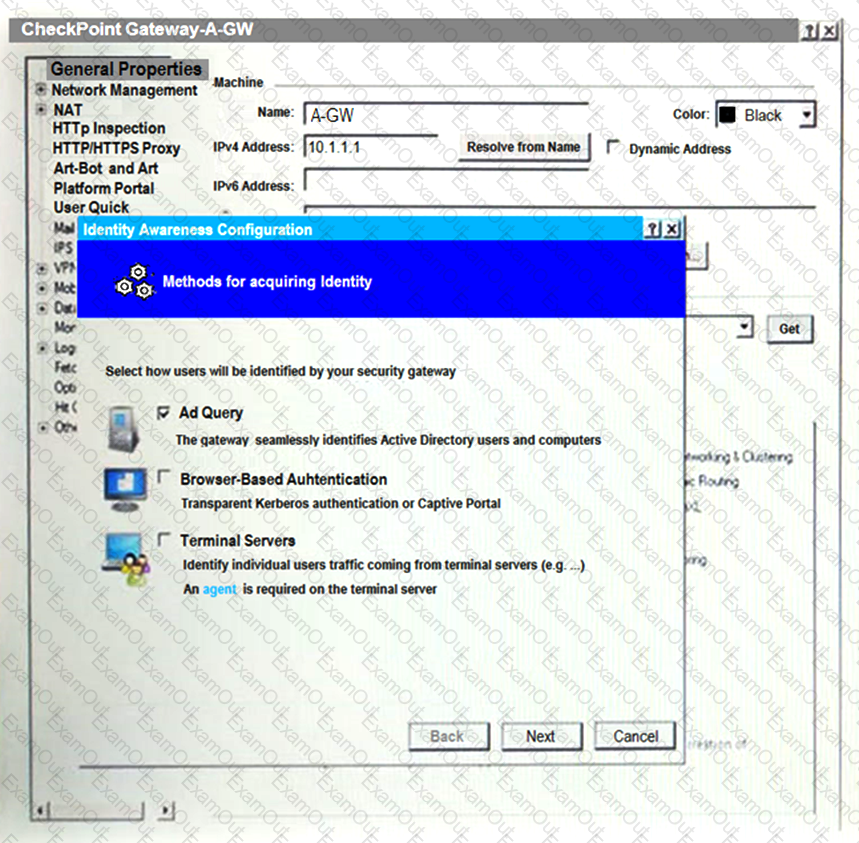
After clicking “Next” the above configuration is supported by:
True or False: In R81, more than one administrator can login to the Security Management Server with write permission at the same time.
In which scenario will an administrator need to manually define Proxy ARP?
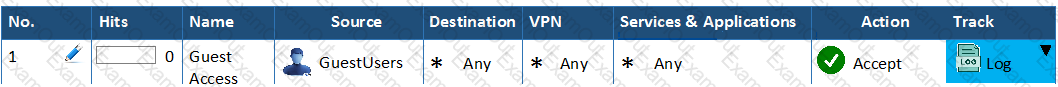
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
What is the biggest benefit of policy layers?
What is the main objective when using Application Control?
Fill in the blank: Authentication rules are defined for ________ .
What are the Threat Prevention software components available on the Check Point Security Gateway?
Name the file that is an electronically signed file used by Check Point to translate the features in the license into a code?

