With SecureXL enabled, accelerated packets will pass through the following:
What are the methods of SandBlast Threat Emulation deployment?
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
You have a Gateway is running with 2 cores. You plan to add a second gateway to build a cluster and used a device with 4 cores.
How many cores can be used in a Cluster for Firewall-kernel on the new device?
When SecureXL is enabled, all packets should be accelerated, except packets that match the following conditions:
Which tool is used to enable ClusterXL?
What will SmartEvent automatically define as events?
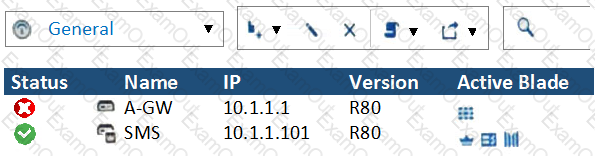
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)
Which path below is available only when CoreXL is enabled?
Check Point APIs allow system engineers and developers to make changes to their organization’s security policy with CLI tools and Web Services for all the following except:
What statement best describes the Proxy ARP feature for Manual NAT in R81.20?
What is the command to show SecureXL status?
One of major features in R81 SmartConsole is concurrent administration.
Which of the following is NOT possible considering that AdminA, AdminB and AdminC are editing the same Security Policy?
Check Point security components are divided into the following components:

