Which of the following is NOT a component of Check Point Capsule?
When should you generate new licenses?
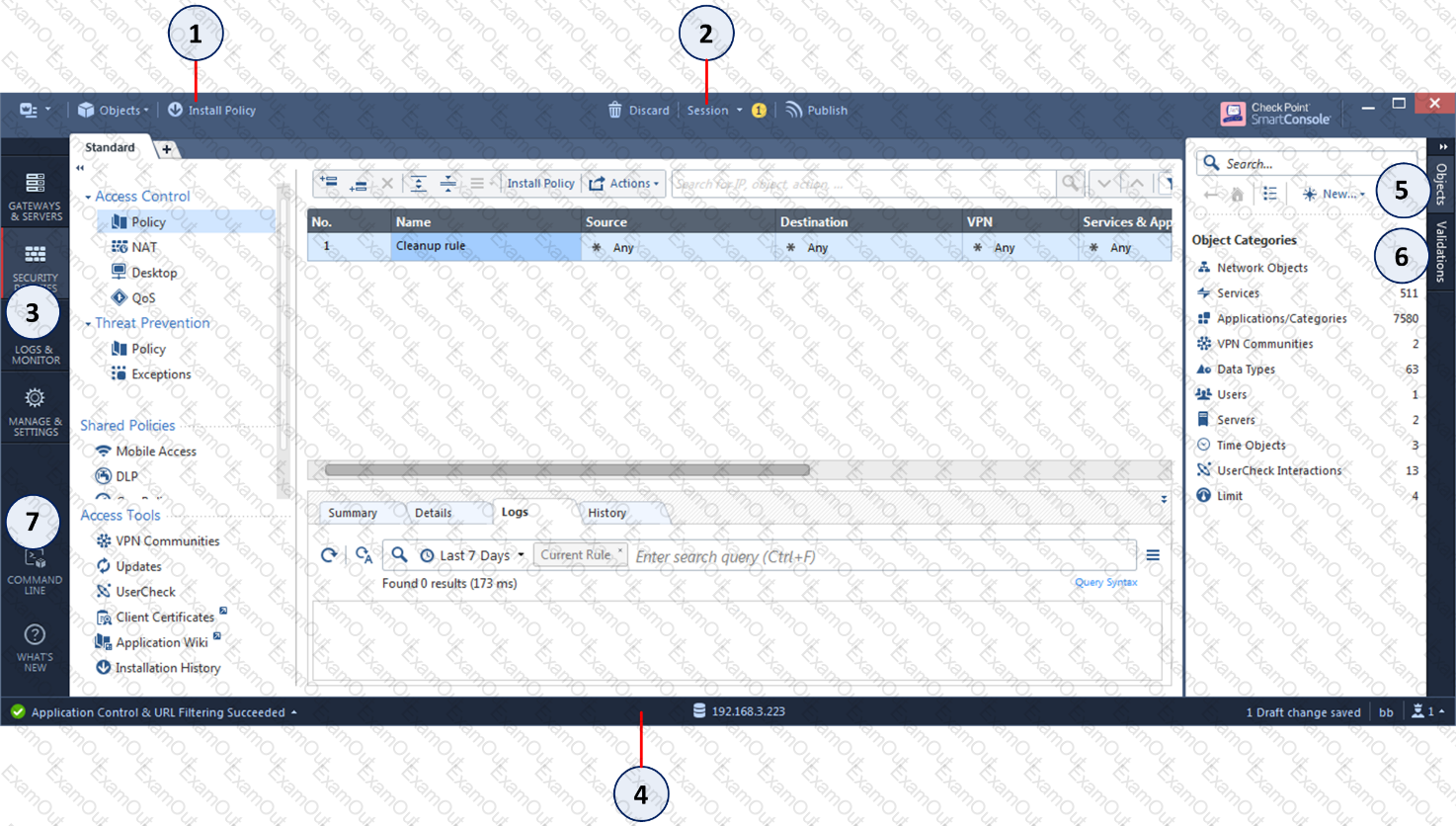
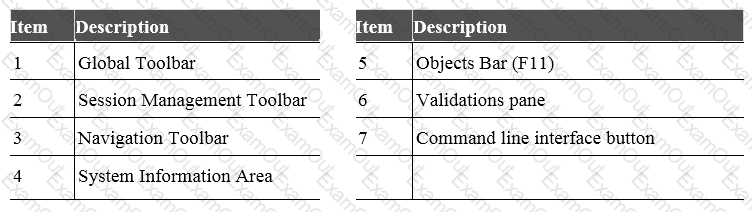
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
With URL Filtering, what portion of the traffic is sent to the Check Point Online Web Service for analysis?
What command from the CLI would be used to view current licensing?
Which message indicates IKE Phase 2 has completed successfully?
Which of the following is considered to be the more secure and preferred VPN authentication method?
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
When configuring Anti-Spoofing, which tracking options can an Administrator select?
A layer can support different combinations of blades What are the supported blades: