If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer
Fill in the blanks: Gaia can be configured using _______ the ________.
What is the user ID of a user that have all the privileges of a root user?
Which of the following cannot be configured in an Access Role Object?
Fill in the blank: In order to install a license, it must first be added to the ____________.
You can see the following graphic:
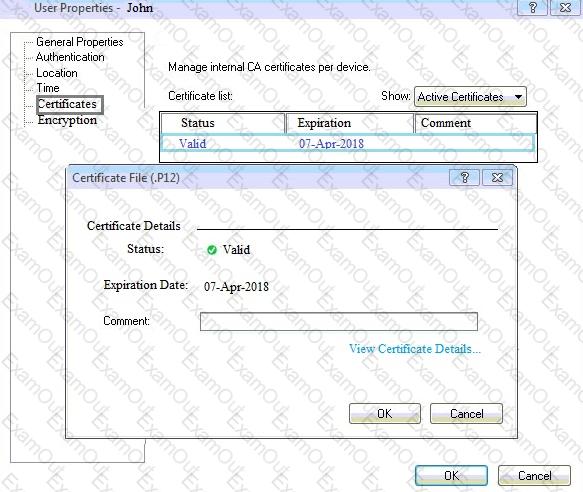
What is presented on it?
Core Protections are installed as part of what Policy?
Which Check Point supported authentication scheme typically requires a user to possess a token?
What default layers are included when creating a new policy layer?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.

