Which of the following is most likely to address a problem with an operating system's ability to withstand an attack that attempts to exploit a buffer overflow?
What is the primary drawback of using symmetric-key encryption?
Consider the following diagram involving two firewall-protected networks:
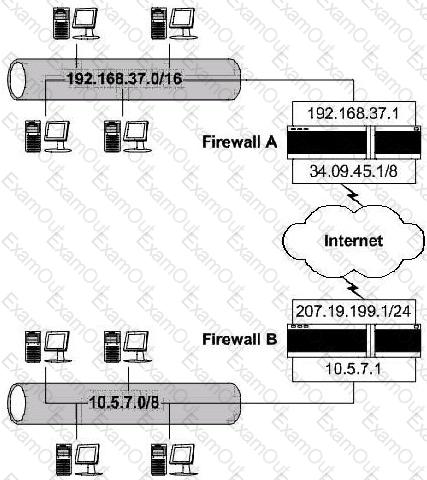
Which of the following is necessary for each of the firewalls to allow private IP addresses to be passed on to the Internet?
A new video conferencing device has been installed on the network. You have been assigned to troubleshoot a connectivity problem between remote workers and the central company. Specifically, remote workers are having problems making any connection at all. Which technique will most likely help you solve this problem while retaining the existing level of security at the firewall?
Which of the following organizations provides regular updates concerning security breaches and issues?
An application is creating hashes of each file on an attached storage device. Which of the following will typically occur during this process?
Which of the following activities is the most effective at keeping the actions of nae end users from putting the company's physical and logicalWhich of the following activities is the most effective at keeping the actions of na?e end users from putting the company's physical and logical resources at risk?
Consider the following series of commands from a Linux system: iptables -A input -p icmp -s 0/0 -d 0/0 -j REJECT Which explanation best describes the impact of the resulting firewall ruleset?

