You need to update an existing AWS CloudFormation stack. If needed, a copy to the CloudFormation template is available in an Amazon SB bucket named cloudformation-bucket
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. update the Amazon EQ instance named Devinstance by making the following changes to the stack named 1700182:
a) Change the EC2 instance type to us-east-t2.nano.
b) Allow SSH to connect to the EC2 instance from the IP address range
192.168.100.0/30.
c) Replace the instance profile IAM role with IamRoleB.
4. Deploy the changes by updating the stack using the CFServiceR01e role.
5. Edit the stack options to prevent accidental deletion.
6. Using the output from the stack, enter the value of the Prodlnstanceld in the text box below:
A webpage is stored in an Amazon S3 bucket behind an Application Load Balancer (ALB). Configure the SS bucket to serve a static error page in the event of a failure at the primary site.
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. There is an existing hosted zone named lab-
751906329398-26023898.com that contains an A record with a simple routing policy that routes traffic to an existing ALB.
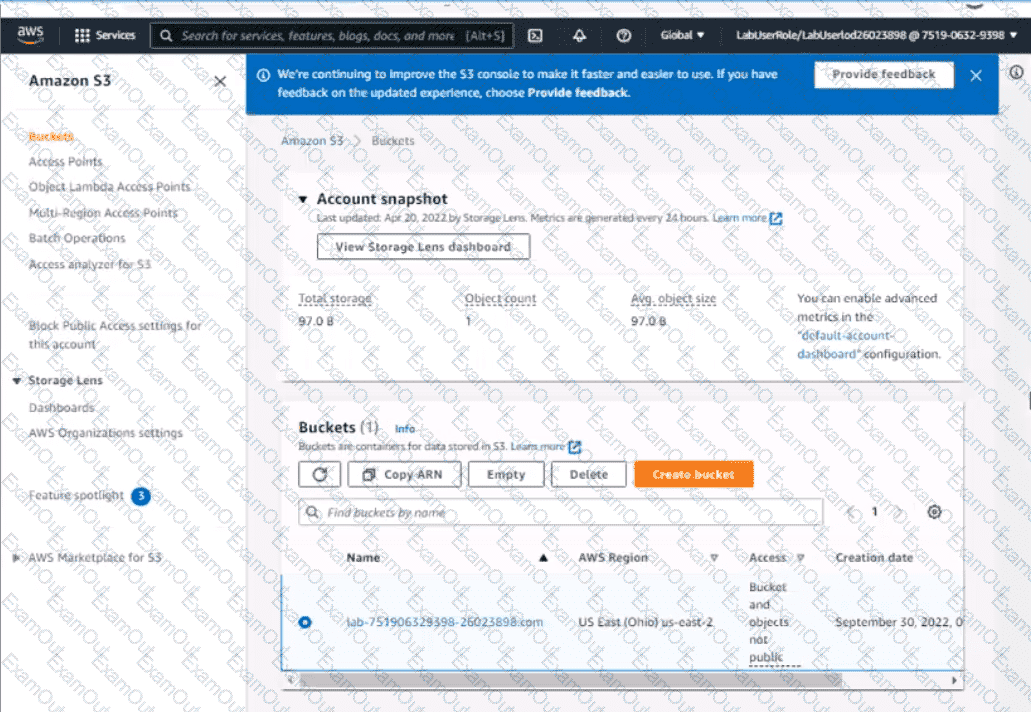
4. Configure the existing S3 bucket named lab-751906329398-26023898.com as a static hosted website using the object named index.html as the index document
5. For the index-html object, configure the S3 ACL to allow for public read access. Ensure public access to the S3 bucketjs allowed.
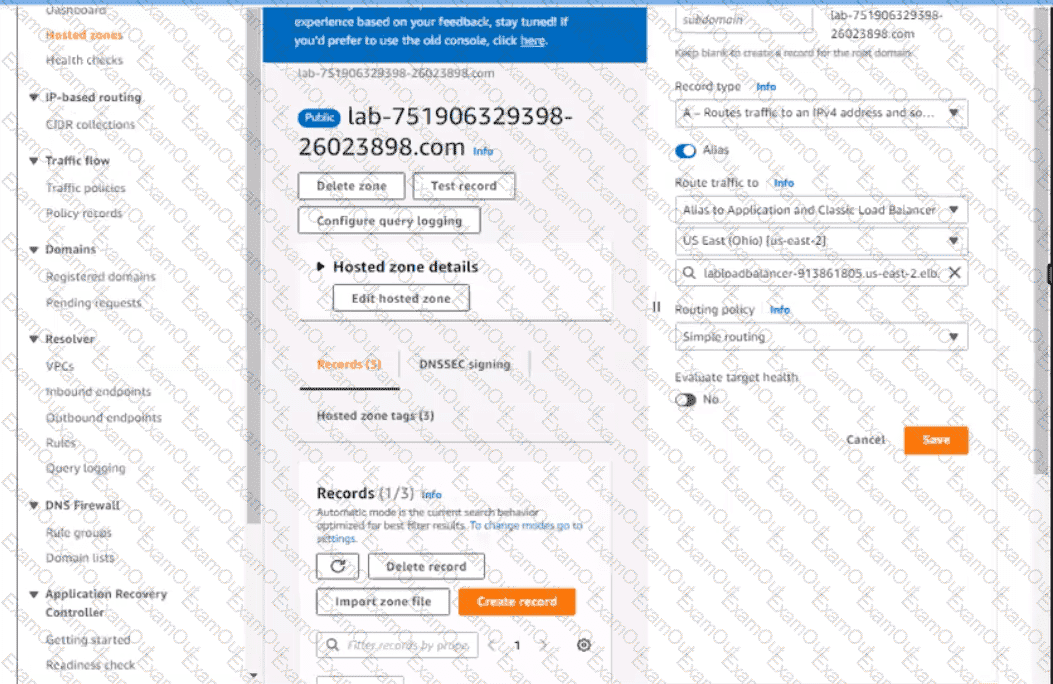
6. In Amazon Route 53, change the A record for domain lab-751906329398-26023898.com to a primary record for a failover routing policy. Configure the record so that it evaluates the health of the ALB to determine failover.
7. Create a new secondary failover alias record for the domain lab-751906329398-26023898.com that routes traffic to the existing 53 bucket.
If your AWS Management Console browser does not show that you are logged in to an AWS account, close the browser and relaunch the
console by using the AWS Management Console shortcut from the VM desktop.
If the copy-paste functionality is not working in your environment, refer to the instructions file on the VM desktop and use Ctrl+C, Ctrl+V or Command-C , Command-V.
Configure Amazon EventBridge to meet the following requirements.
1. use the us-east-2 Region for all resources,
2. Unless specified below, use the default configuration settings.
3. Use your own resource naming unless a resource
name is specified below.
4. Ensure all Amazon EC2 events in the default event
bus are replayable for the past 90 days.
5. Create a rule named RunFunction to send the exact message every 1 5 minutes to an existing AWS Lambda function named LogEventFunction.
6. Create a rule named SpotWarning to send a notification to a new standard Amazon SNS topic named TopicEvents whenever an Amazon EC2
Spot Instance is interrupted. Do NOT create any topic subscriptions. The notification must match the following structure:
Input Path:
{“instance” : “$.detail.instance-id”}
Input template:
“ The EC2 Spot Instance
Application A runs on Amazon EC2 instances behind a Network Load Balancer (NLB). The EC2 instances are in an Auto Scaling group and are in the same subnet that is associated with the NLB. Other applications from an on-premises environment cannot communicate with Application A on port 8080.
To troubleshoot the issue, a SysOps administrator analyzes the flow logs. The flow logs include the following records:
What is the reason for the rejected traffic?
A company has deployed a web application in a VPC that has subnets in three Availability Zones. The company launches three Amazon EC2 instances from an
EC2 Auto Scaling group behind an Application Load Balancer (ALB).
A SysOps administrator notices that two of the EC2 instances are in the same Availability Zone, rather than being distributed evenly across all three Availability
Zones. There are no errors in the Auto Scaling group's activity history.
What is the MOST likely reason for the unexpected placement of EC2 instances?
A SysOps Administrator is managing a web application that runs on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances run in an
EC2 Auto Scaling group. The administrator wants to set an alarm for when all target instances associated with the ALB are unhealthy.
Which condition should be used with the alarm?
A company migrates a write-once, read-many (WORM) drive to an Amazon S3 bucket that has S3 Object Lock configured in governance mode. During the migration, the company copies unneeded data to the S3 bucket.
A SysOps administrator attempts to delete the unneeded data from the S3 bucket by using the AWS CLI. However, the SysOps administrator receives an error.
Which combination of steps should the SysOps administrator take to successfully delete the unneeded data? (Select TWO.)
A company has an Amazon EC2 instance that supports a production system. The EC2 instance is backed by an Amazon Elastic Block Store (Amazon EBS) volume. The EBS volume's drive has filled to 100% capacity, which is causing the application on the EC2 instance to experience errors.
Which solution will remediate these errors in the LEAST amount of time?
A company uses AWS CloudFormation to manage a stack of Amazon EC2 instances on AWS. A SysOps administrator needs to keep the instances and all of the instances’ data, even if someone deletes the stack.
Which solution will meet these requirements?
A company is creating a new multi-account architecture. A Sysops administrator must implement a login solution to centrally manage
user access and permissions across all AWS accounts. The solution must be integrated with AWS Organizations and must be connected to a third-party Security Assertion Markup Language (SAML) 2.0 identity provider (IdP).
What should the SysOps administrator do to meet these requirements?

 Graphical user interface, application, Teams Description automatically generated
Graphical user interface, application, Teams Description automatically generated