A company has AWS accounts in an organization in AWS Organizations. The organization includes a dedicated security account.
All AWS account activity across all member accounts must be logged and reported to the dedicated security account. The company must retain all the activity logs in a secure storage location within the dedicated security account for 2 years. No changes or deletions of the logs are allowed.
Which combination of steps will meet these requirements with the LEAST operational overhead? (Select TWO.)
A company operates an Amazon EC2 instance that is registered as a target of a Network Load Balancer (NLB). The NLB is associated with a security group. The security group allows inbound TCP traffic on port 22 from 10.0.0.0/23.
The company maps the NLB to two subnets that share the same network ACL and route table. The route table has a route for 0.0.0.0/0 to an internet gateway. The network ACL has one inbound rule that has a priority of 20 and that allows TCP traffic on port 22 from 10.0.0.0/16.
A security engineer receives an alert that there is an unauthorized SSH session on the EC2 instance. The unauthorized session originates from 10.0.1.5. The company's incident response procedure requires unauthorized SSH sessions to be immediately interrupted. The instance must remain running, and its memory must remain intact.
Which solution will meet these requirements?
A security engineer wants to forward custom application-security logs from an Amazon EC2 instance to Amazon CloudWatch. The security engineer installs the CloudWatch agent on the EC2 instance and adds the path of the logs to the CloudWatch configuration file.
However, CloudWatch does not receive the logs. The security engineer verifies that the awslogs service is running on the EC2 instance.
What should the security engineer do next to resolve the issue?
A company has several Amazon S3 buckets that do not enforce encryption in transit. A security engineer must implement a solution that enforces encryption in transit for all the company's existing and future S3 buckets.
Which solution will meet these requirements?
A company is running a containerized application on an Amazon Elastic Container Service (Amazon ECS) cluster that uses AWS Fargate. The application runs as several ECS services. The ECS services are in individual target groups for an internet-facing Application Load Balancer (ALB). The ALB is the origin for an Amazon CloudFront distribution. An AWS WAF web ACL is associated with the CloudFront distribution.
Web clients access the ECS services through the CloudFront distribution. The company learns that the web clients can bypass the web ACL and can access the ALB directly.
Which solution will prevent the web clients from directly accessing the ALB?
A security engineer for a company is investigating suspicious traffic on a web application in the AWS Cloud. The web application is protected by an Application Load Balancer (ALB) behind an Amazon CloudFront distribution. There is an AWS WAF web ACL associated with the ALB. The company stores AWS WAF logs in an Amazon S3 bucket.
The engineer notices that all incoming requests in the AWS WAF logs originate from a small number of IP addresses that correspond to CloudFront edge locations. The security engineer must identify the source IP addresses of the clients that are initiating the suspicious requests.
Which solution will meet this requirement?
A company uses AWS IAM Identity Center with SAML 2.0 federation. The company decides to change its federation source from one identity provider (IdP) to another. The underlying directory for both IdPs is Active Directory.
Which solution will meet this requirement?
A security engineer is responding to an incident that is affecting an AWS account. The ID of the account is 123456789012. The attack created workloads that are distributed across multiple AWS Regions.
The security engineer contains the attack and removes all compute and storage resources from all affected Regions. However, the attacker also created an AWS KMS key. The key policy on the KMS key explicitly allows IAM principal kms:* permissions.
The key was scheduled to be deleted the previous day. However, the key is still enabled and usable. The key has an ARN of
arn:aws:kms:us-east-2:123456789012:key/mrk-0bb0212cd9864fdea0dcamzo26efb5670.
The security engineer must delete the key as quickly as possible.
Which solution will meet this requirement?
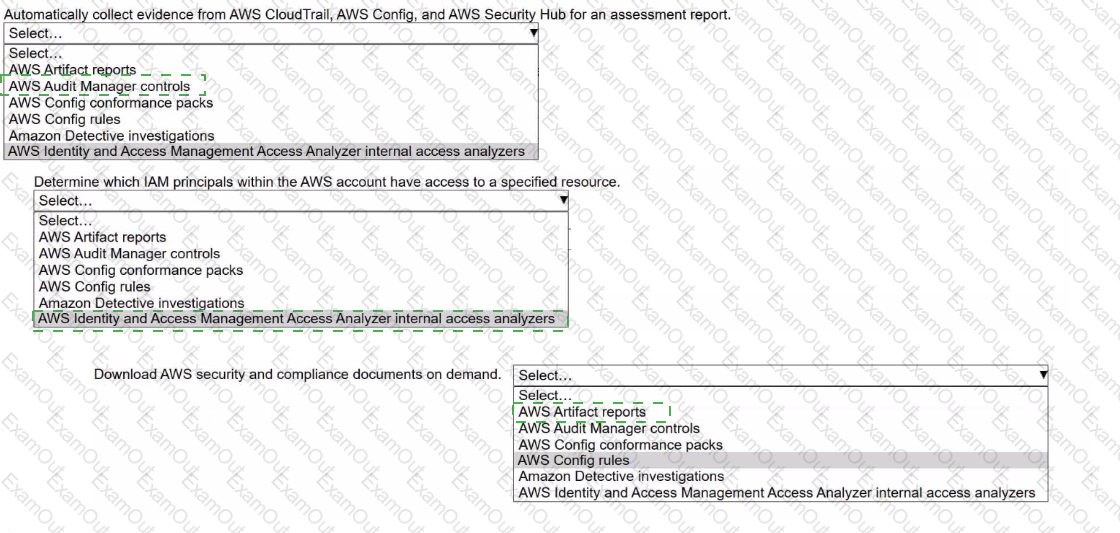
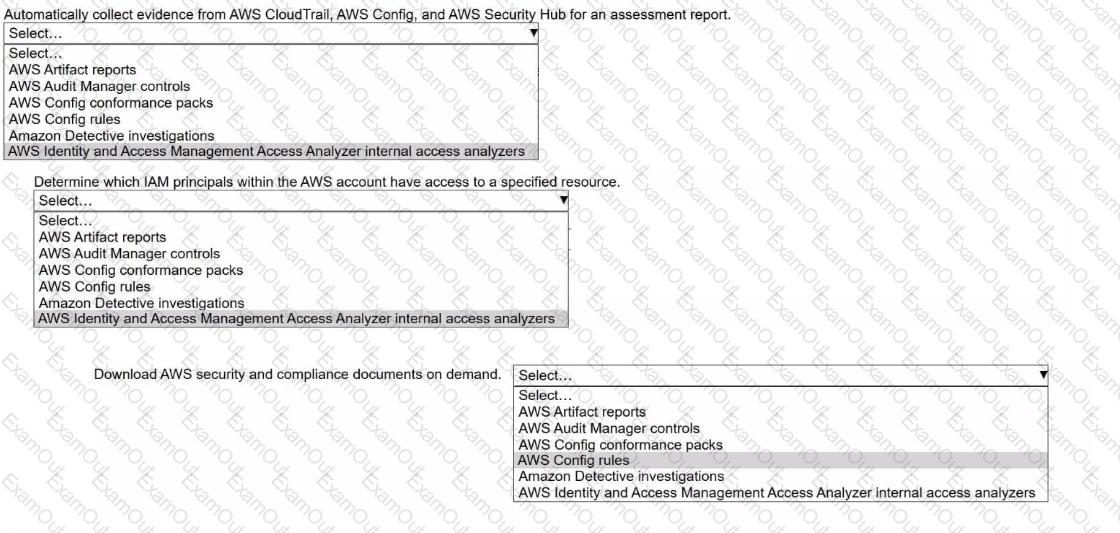
A security engineer needs to prepare for a security audit of an AWS account.
Select the correct AWS resource from the following list to meet each requirement. Select each resource one time or not at all. (Select THREE.)
• AWS Artifact reports
• AWS Audit Manager controls
• AWS Config conformance packs
• AWS Config rules
• Amazon Detective investigations
• AWS Identity and Access Management Access Analyzer internal access analyzers
A security engineer needs to prepare a company's Amazon EC2 instances for quarantine during a security incident. The AWS Systems Manager Agent (SSM Agent) has been deployed to all EC2 instances. The security engineer has developed a script to install and update forensics tools on the EC2 instances.
Which solution will quarantine EC2 instances during a security incident?