Which of the following statements describes an advantage of bi-directional traceability between requirements / user stories and test cases?
What is a common way to use business process modeling for ATDD?
Which of the following statements about test approaches and test techniques for acceptance testing is MOST correct?
Which one of the following combinations between high-level security requirements and security testing techniques matches BEST?
As an acceptance tester, you are stuck between two stakeholders that demand contradicting acceptance criteria
Which one of the following actions is MOST promising to resolve the conflict?
On a project to develop an event booking platform, a review session is being conducted on acceptance test cases written in Ghenkin's language. Consider the following test case:
1. GIVEN I am logged in on the event booking platform
2. AND I have selected an event from the list displayed for the "live concert" category
3. WHEN I click "Buy Tickets" buttom
4. AND I enter "3" into "Ticket quantify" field
5. AND I agree on terms and conditions
6. THEN The system should display the checkout page
7. AND I should provide my personal data for payment and eticket delivery
Which of the following sentences MOST closely corresponds to a comment that could be made on this test case during the review?
As a tester you participate in the project of the decision support system for granting a loan. You are asked to review the acceptance criteria for the following requirement:
REQ 3.28. The automated system records critical credit application data (CCAD. needed to support application screening.
Assume that it is well known what kind of data CCAD are. Which of the following would be the BEST example of an acceptance criterion for this requirement?
Which of the following statements BEST describes the relationship between beta testing and acceptance testing?
Which of the following sentences explains BEST how business process and business rule modeling can be used for ATDD?
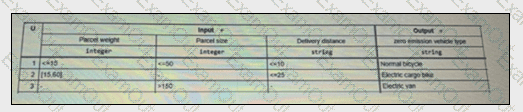
A green courier working for an urban delivery service company uses three types of vehicles: normal bicycles, electric cargo bikes and electric vans. The following DMN table provides the rules used to select the type of zero emission vehicle to be used according to the weight (in kg) and the largest dimension (in cm) of the parcel, and the delivery distance (in km)
Which one of the following statements is consistent with this DMN table?