Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
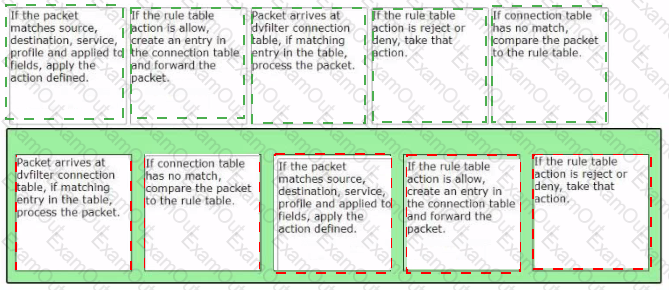
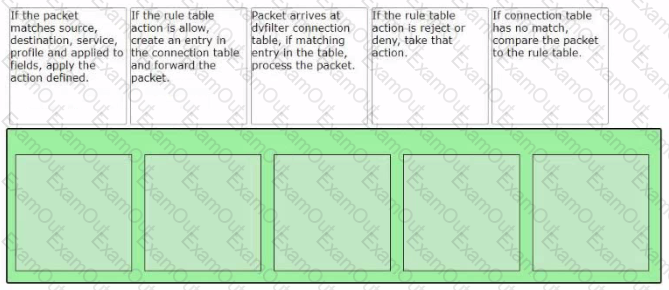
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
Which two are supported by L2 VPN clients? (Choose two.)
What is the most restrictive NSX built-in role which will allow a user to apply configuration changes on an NSX Edge?
When a stateful service is enabled for the first time on a Tier-0 Gateway, what happens on the NSX Edge node?
Which NSX feature can be leveraged to achieve consistent policy configuration and simplicity across sites?
Which three DHCP Services are supported by NSX? (Choose three.)
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
An NSX administrator has deployed a single NSX Manager node and will be adding two additional nodes to form a 3-node NSX Management Cluster for a production environment. The administrator will deploy these two additional nodes and Cluster VIP using the NSX UI.
What two are the prerequisites for this configuration? (Choose two.)