Application Settings allow you to____________.
If a customer reports an issue with their order, an Investigation case is created. All investigation cases are higher priority than other case types.
What configuration supports this requirement?
You configure a child case to override the locking strategy of the parent case. The parent case has a time-out value of one hour.
Which time-out value option is recommended for the child case?
Which two actions do you perform when using the Performance Analyzer (PAL) to ensure that you obtain accurate performance data? (Choose Two)
A hospital uses a case type to manage the treatment of patients visiting the Emergency Room (ER). Cases are created when the patient checks in at the registration desk, and are resolved when the patient is released from the hospital. Stakeholders identify the following security requirements for the case type.
♦ Patients access cases on a read-only basis.
♦ Patients can only access their own cases.
♦ Doctors and nurses can modify cases throughout the case life cycle.
♦ Only doctors are allowed to write prescriptions.
What two steps, when performed together, allow you to ensure that patients can read, but not edit, cases? (Choose Two)
Which two statements are valid about configuring Pega Web Mashup? (Choose Two)
You are analyzing application performance and identify a data transform exceeding preferred performance parameters. Which performance tool do you use to help troubleshoot the issue?
A developer has identified resource-intensive queue processors as the source of performance issues that application users are experiencing.
Which two actions do you perform to resolve the performance issues? (Choose Two)
What are three valid ways to exchange data through a Pega Web Mashup? (Choose Three)
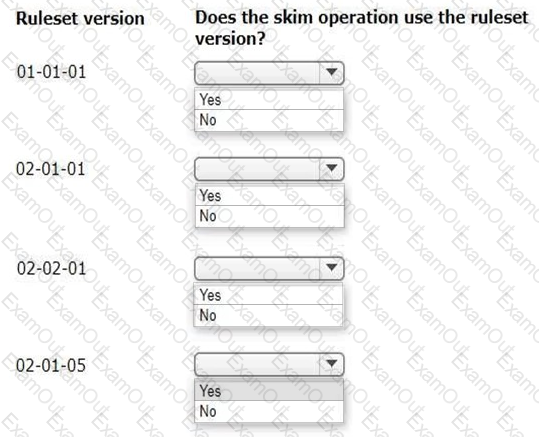
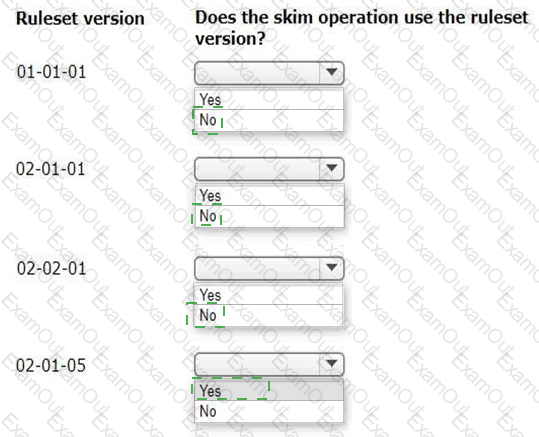
You perform a major skim on the ruleset ABC:02-02 to ABC:03-01.
In the Answer area, select the ruleset versions that the skim operation uses.