can you create a custom compliance standard in Prisma Public Cloud?
Which two types of Resource Query Language (RQL) queries can be used to create policies? (Choose two.)
An Azure VNet has the IP network 10.0.0.0/16 with two subnets, 10.0.1.0/24 (used for web servers) and 10.0.2.0/24 (used for database servers). Which is a valid IP address to manage the VM-Series NGFW?
A client has a sensitive internet-facing application server in Microsoft Azure and is concerned about resource exhaustion because of distributed denial-of-service attacks What can be configured on the VM-Series firewall to specifically protect this server against this type of attack?
What are two business values of Cloud Code Security? (Choose two.)
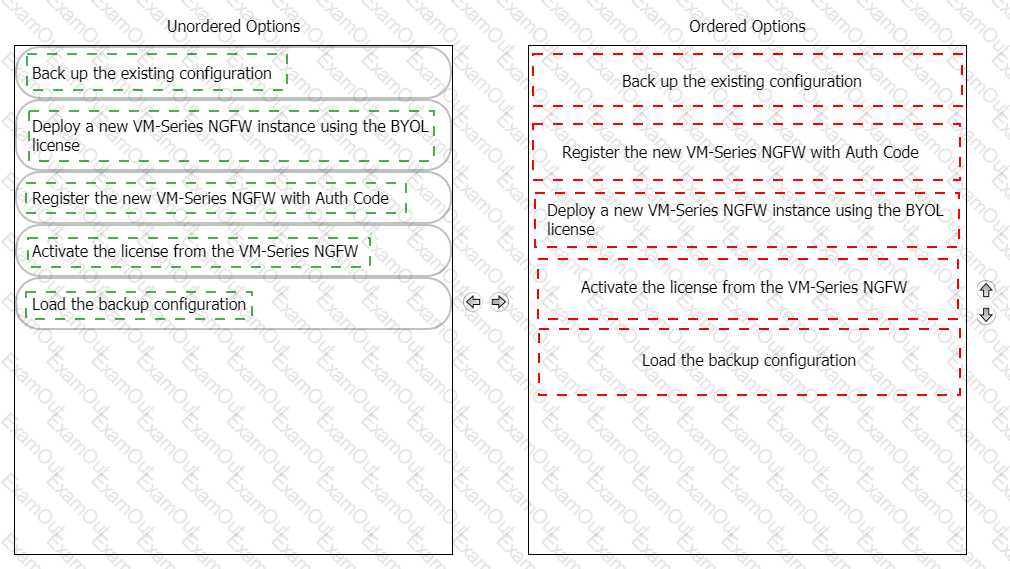
A customer has deployed a VM-Series NGFW on Amazon Web Services using a PAYG license. What is the sequence required by the customer to switch to a BYOL license?
Which statement applies to vulnerability management policies?
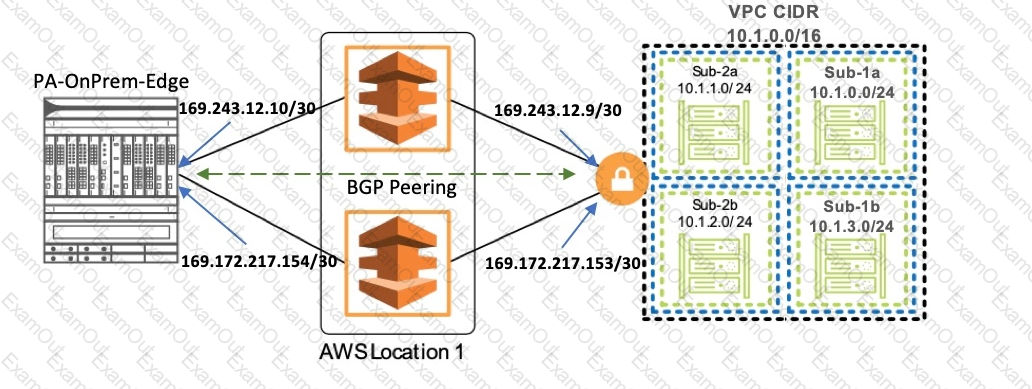
Based on the diagram, how many routes will the virtual gateway advertise to the on-premises NGFW over the Amazon Web Services Direct Connect link?
What does Infrastructure as Code (laC) collect to enable automation?
All Amazon Regional Database Service (RDS)-deployed resources and the regions in which they are deployed can be identified by prisma Cloud using which two methods? (Choose two.)