Which statement best describes the benefits of the combination of Prisma Cloud, Cortex Xpanse, and partner services?
When analyzing logs for indicators, which are used for only BIOC identification'?
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
When integrating with Splunk, what will allow you to push alerts into Cortex XSOAR via the REST API?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
Which two filter operators are available in Cortex XDR? (Choose two.)
Which two entities can be created as a BIOC? (Choose two.)
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
What is the result of creating an exception from an exploit security event?
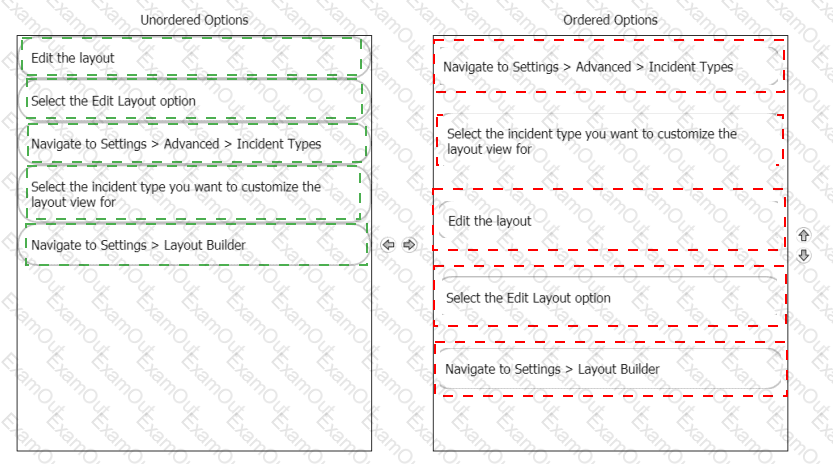
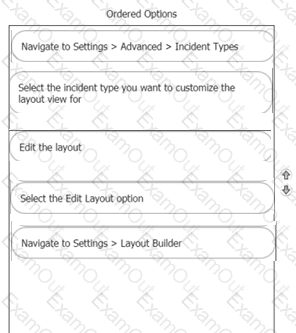
Rearrange the steps into the correct order for modifying an incident layout.

 Correct
Correct