A network administrator created an intrazone Security policy rule on the firewall. The source zones were set to IT. Finance, and HR.
Which two types of traffic will the rule apply to? (Choose two)
Which Security policy action will message a user's browser that their web session has been terminated?
Where within the firewall GUI can all existing tags be viewed?
What can be achieved by disabling the Share Unused Address and Service Objects with Devices setting on Panorama?
During the App-ID update process, what should you click on to confirm whether an existing policy rule is affected by an App-ID update?
An administrator manages a network with 300 addresses that require translation. The administrator configured NAT with an address pool of 240 addresses and found that connections from addresses that needed new translations were being dropped.
Which type of NAT was configured?
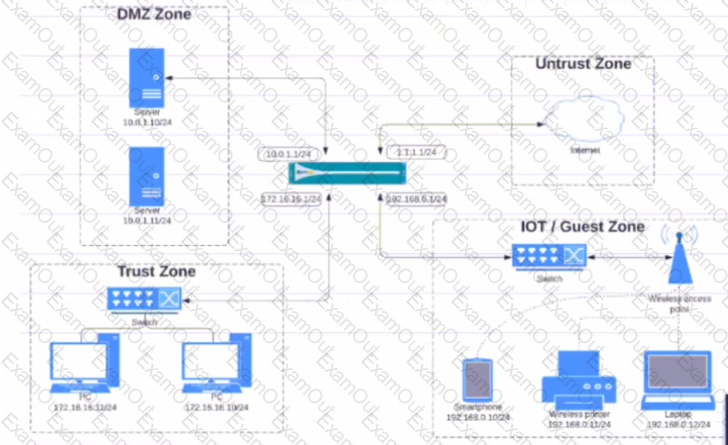
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH. web-browsing and SSL applications
Which policy achieves the desired results?
A)

B)
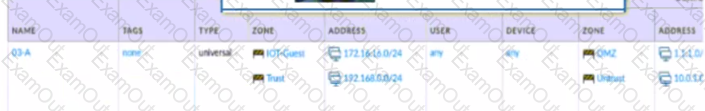
C)

D)

Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
Which type of security policy rule will match traffic that flows between the Outside zone and inside zone, but would not match traffic that flows within the zones?
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)

