Which action results in the firewall blocking network traffic without notifying the sender?
You must configure which firewall feature to enable a data-plane interface to submit DNS queries on behalf of the control plane?
What are three configurable interface types for a data-plane ethernet interface? (Choose three.)
Which two addresses should be reserved to enable DNS sinkholing? (Choose two.)
An administrator is implementing an exception to an external dynamic list by adding an entry to the list manually. The administrator wants to save the changes, but the OK button is grayed out.
What are two possible reasons the OK button is grayed out? (Choose two.)
In which three places on the PAN-OS interface can the application characteristics be found? (Choose three.)
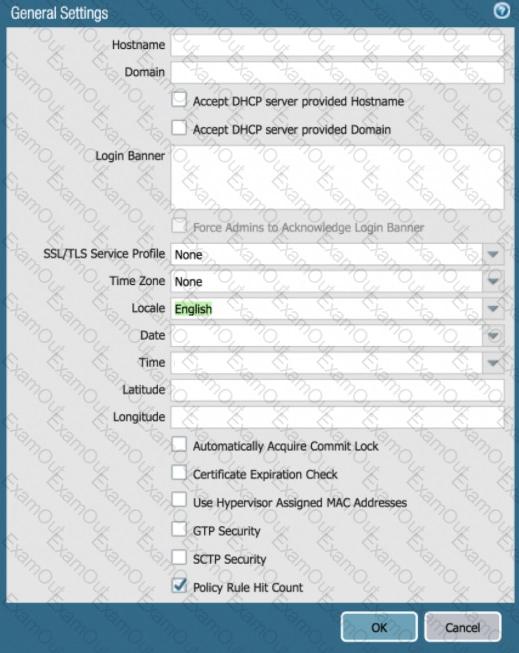
Based on the graphic, what is the purpose of the SSL/TLS Service profile configuration option?
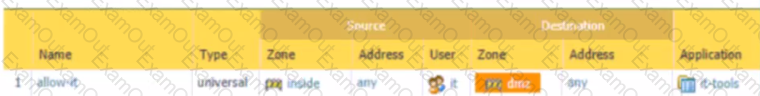
Based on the screenshot what is the purpose of the group in User labelled ''it"?
Which solution is a viable option to capture user identification when Active Directory is not in use?
Which action can be performed when grouping rules by group tags?

