The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
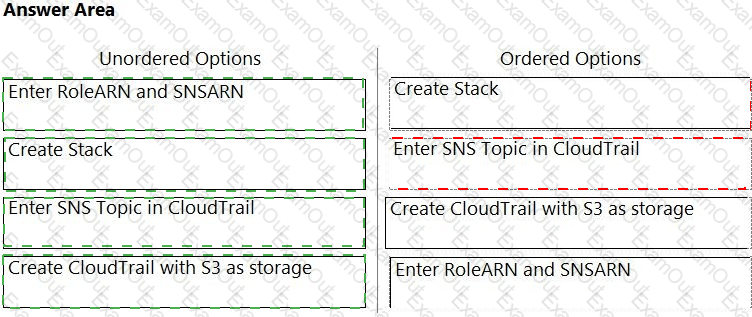
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
Which container image scan is constructed correctly?
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?