Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three).
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
What is an example of an outbound notification within Prisma Cloud?
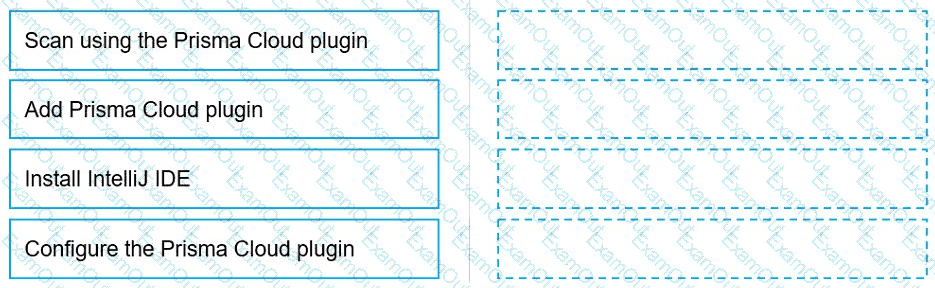
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
Where can Defender debug logs be viewed? (Choose two.)
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
A customer wants to scan a serverless function as part of a build process. Which twistcli command can be used to scan serverless functions?


