Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
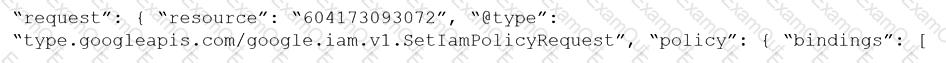
B)
C)
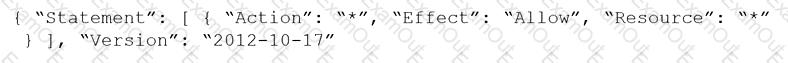
D)

Which three types of runtime rules can be created? (Choose three.)
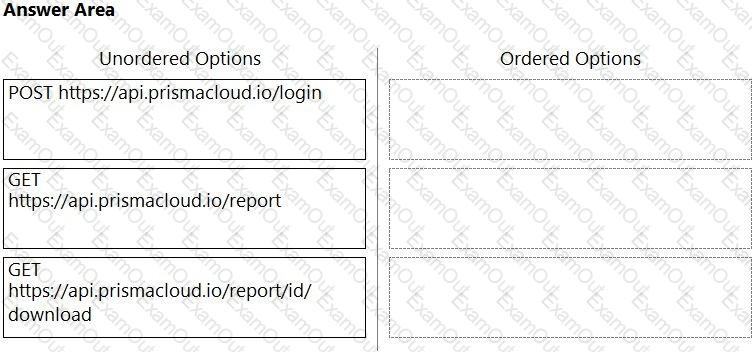
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
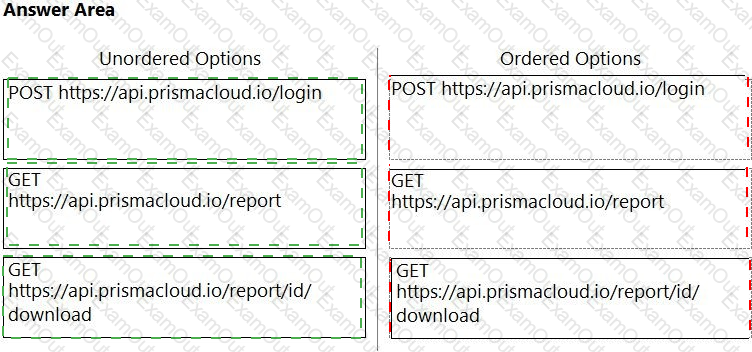
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
What are two ways to scan container images in Jenkins pipelines? (Choose two.)
Under which tactic is “Exploit Public-Facing Application” categorized in the ATT&CK framework?
What is required for Prisma Cloud to successfully execute auto-remediation commands?
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?