What is the correct syntax for using transparent data encryption with an existing InnoDB table?
Examine these InnoDB Cluster parameter settings:
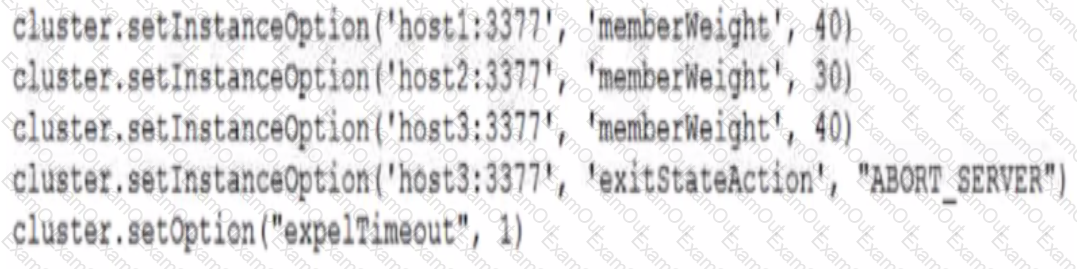
Now examine the partial status:

A permanent network failure isolates host3.
Which two statements are true? (Choose two.)
Which two are true about binary logs used in asynchronous replication? (Choose two.)
Which three are types of InnoDB tablespaces? (Choose three.)
Examine this statement and output:
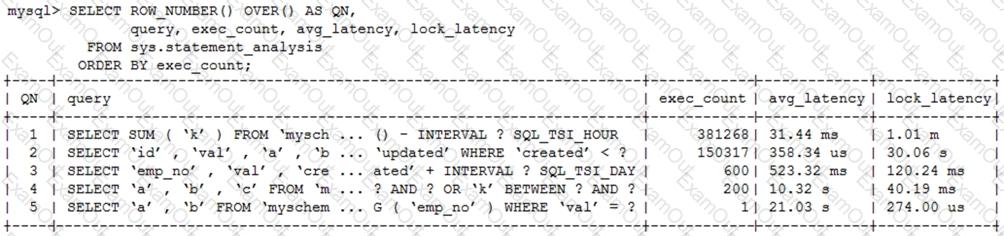
You must try to reduce query execution time.
Which two queries should you focus on? (Choose two.)
User account baduser@hostname on your MySQL instance has been compromised.
Which two commands stop any new connections using the compromised account? (Choose two.)
What does the slave I/O thread do?
Which condition is true about the use of the hash join algorithm?
Which two statements are true about MySQL server multi-source replication? (Choose two.)
A MySQL server is monitored using MySQL Enterprise Monitor’s agentless installation.
Which three features are available with this installation method? (Choose three.)

