Which storage option for MySQL data directory typically offers the worst performance in a highly concurrent, OLTP-heavy, IO-bound workload?
Consider the table people with this definition:
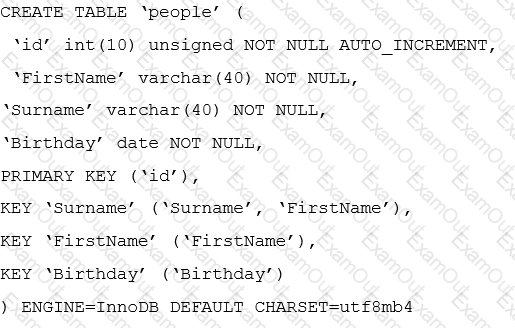
The application uses a query such as:
SELECT * FROM people WHERE YEAR(Birthday) = 1980;
The query is not using an index.
Which two methods can be used to allow the query to use an index? (Choose two.)
Consider:

What does the range value in the type column mean?
Examine the mysqldumpslow output:
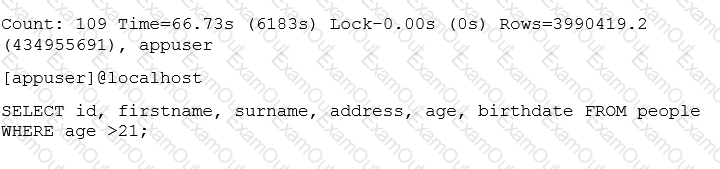
Which two options could explain the slow query? (Choose two.)
Which MySQL utility program should you use to process and sort the Slow Query Log based on query time or average query time?
You are asked to examine user accounts and find:
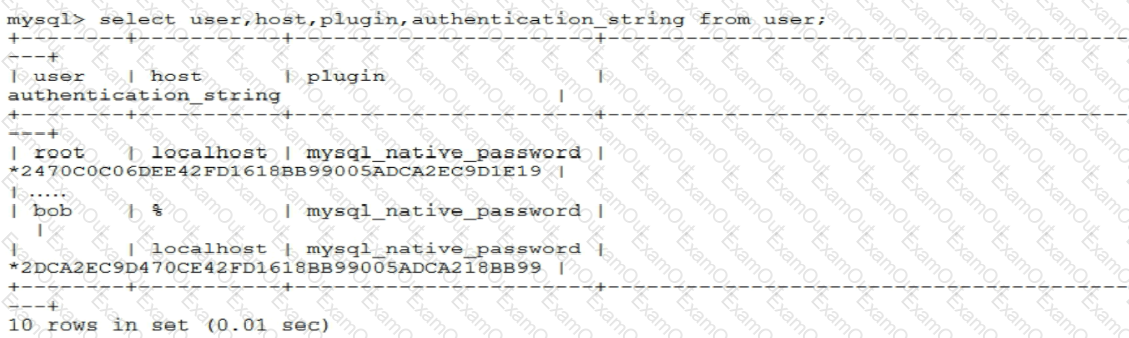
Which two statements will best secure this environment? (Choose two.)
On a master server that is using statement-based replication, a table of log data has become very large.
You decide to delete 100,000 rows.
Which two methods can be independently invoked to ensure that the delete is properly propagated to the slave? (Choose two.)
What two statements are true regarding FLUSH TABLES FOR EXPORT? (Choose two.)
Which statement is true about using Microsoft Windows Cluster as a platform for MySQL?
You will configure a MySQL Server to act as a replication master. Which two options must be configured correctly to allow this? (Choose two.)

