Task 2: Create a Compute Instance and Install the Web Server
Create a compute instance, where:
Name: PBT-CERT-VM-01
Image: Oracle Linux 8
Shape: VM.Standard.A1.Flex
Subnet: Compute-Subnet-PBT-CERT
Install and configure Apache web server:
a.
Install Apache
sudo yum -y install httpd
b.
Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
2. Install and configure Apache web server:
a. Install Apache
sudo yum -y install httpd
b. Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
c. Configure firewall to allow HTTP traffic (port 80)
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --reload
d. Create an index.html file
sudo bash -c 'echo You are visiting Web Server 1 >> /var/www/html/index.html'
Enter the OCID of the created compute instance PBT-CERT-VM-01 in the text box below.
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
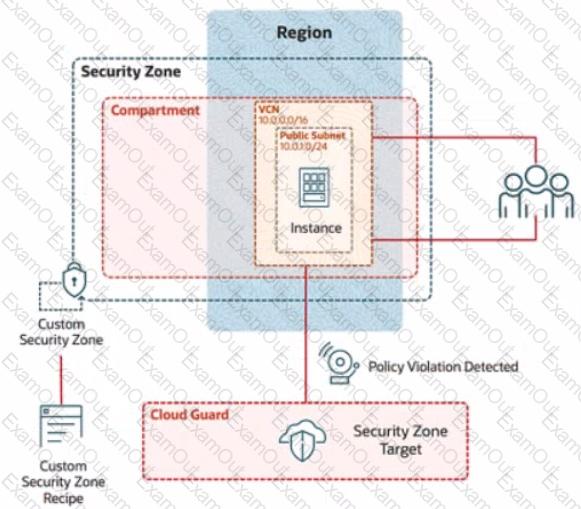
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 2: Create a Security Zone
Create a security Zone named IAD_SAP-PBT-CSZ-01 in your assigned compartement and associate it with the Custom Security Zone Recipe (IAD-SAP-PBT-CSP-01) created in the previous task.
Enter the OCID of the created Security zone in the box below.

A company has deployed OCI Zero Trust Packet Routing (ZPR) to secure its network. They have two compute instances, VM1-01 and VM-02, in a public subnet. VM-01 is tagged with the security attribute app:vm01, and VM-02 is tagged with app:vm02. The VCN is labeled with network:vcn01, The ZPR policy states:

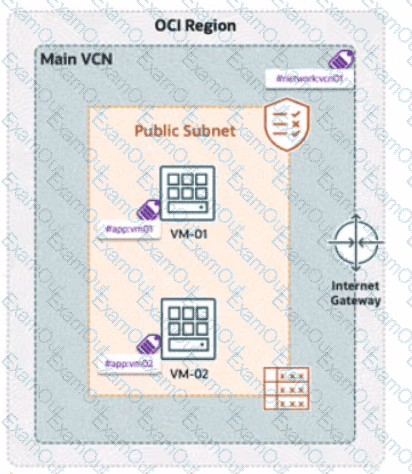
"What is the expected outcome of this policy?
You are a security architect at your organization and have noticed an increase in cyberattacks on your applications, including Cross-Site Scripting (XSS) and SQL Injection. To mitigate these threats, you decide to use OCI Web Application Firewall (WAF).
Which type of OCI WAF rule should you configure to protect against these attacks?
A company has implemented OCI IAM policies with multiple levels of compartments. A policy attached to a parent compartment grants "manage virtual-network-family" permissions. A policy attached to a child compartment grants "use virtual-network-family" permissions.
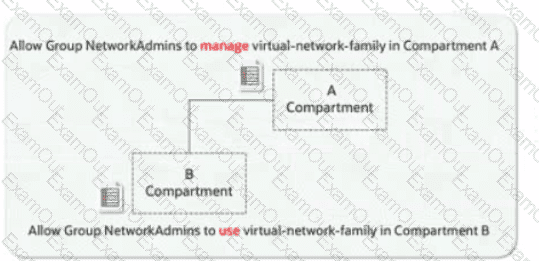
According to OCI IAM policy inheritance, how does the OCI IAM policy engine resolve the permissions for a user attempting to perform an operation that requires 'manage' permissions in the child compartment?
You are the first responder of a security incident for ABC Org. You have identified several IP addresses and URLs in the logs that you suspect may be related to the incident. However, you need more information to confidently determine whether they are indeed malicious or not.
Which OCI service can you use to obtain a more refined information and confidence score for these identified indicators?
"A programmer is developing a Node.js application which will run on a Linux server on their on-premises data center. This application will access various Oracle Cloud Infrastructure (OCI) services using OCI SDKs.
What is the secure way to access OCI services with OCI Identity and Access Management (IAM)?
Task 7: Verify the OCI Certificate with Load Balancer
Verify HTTPS connection to the load balancer by running the following command in Cloud Shell
curl -k https://
Enter the following URL in the web browser:
https://
If prompted with a certificate error, accept the risk and continue.
Verify web page content by ensuring the text, "You are visiting Web Server 1" from the index.html file is displayed in the browser
Task 6: Create Load Balancer and Attach Certificate
Create a Load Balancer with the name PBT-CERT-LB-01 in subnet LB-Subnet-PBT-CERT-SNET-02
Create a Listener for the load balancer, where:
Name: PBT-CERT-LB_LTSN_01
Protocol: HTTPS
Port: 443
Attach the certificate PBT-CERT-01-
Attach the security list PBT-CERT-LB-SL-01 to subnet LB-Subnet-PBT-CERT-SNET-02
Task 5: Create a Certificate
Create a certificate, where:
Certificate name: PBT-CERT-01-
For example, if your username is 99008677-lab.user01, then the certificate name should be PBT-CERT-01990086771abuser01
Ensure you eliminate special characters from the user name.
Common name: PBT-CERT-OCICERT-01
Certificate Authority: PBT-CERT-CA-01 (created in the previous task)

