Which scenario would benefit most from Erasure Coding being enabled on a container?
A guest VM should be able to tolerate simultaneous failure of two nodes or drives.
What are the minimum requirements for the Nutanix cluster?
An administrator manages a cluster and notices several failed components shown in the exhibit.

What two options does the administrator have to run all NCC checks manually? (Choose two.)
An administrator needs to configure a new subnet on an AHV cluster and want to ensure that VMs will automatically be assigned an IP address at creation time.
Which type of network does the administrator need to create?
A customer wants to isolate a group of VMs within their Nutanix environment for security reasons. The customer creates a VM with two NICs to act as a firewall and installs the appropriate software and certificates.
However, no one from the outside can access the application.
What is the likely cause of this problem?
Which method can be used to migrate a VM configured for UEFI-boot from a Nutanix Hyper-V cluster to AHV?
Which three cluster operations require an administrator to reclaim licenses?(Choose three)
What is Prism Central primarily used for?
Refer to the exhibit.
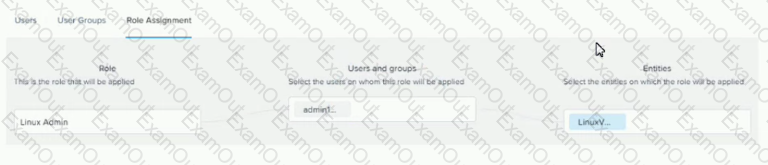
The Linux Admin role has been created to manage only Linux VMs in the environment. However, the Admin1 user does not have access to all Linux VMs.
What step should be taken to grant the proper access?
Which two private key types are supported by the Nutanix SSL certificate implementation? (Choose two.)

