An administrator wants to use Volumes to connect to physical servers that are not able to be virtualized.
Which three things must be configured for Volumes to support iSCSI clients? (Choose three)
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
A node with Erasure Coding fails. What is the impact?
Which expected operations during node addition when the new node has a different AOS version?
Which three configuration scenarios are valid for the deployment of Prism Central? (Choose three.)
What is the default network bond setting for an AHV host configuration?
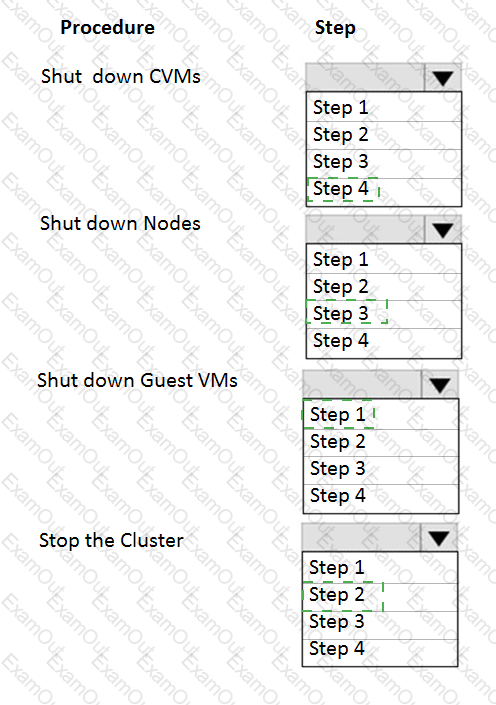
An administrator needs to shut down an AHV cluster to relocate hardware. The administrator upgrades NCC and runs health checks.
Which steps should the administrator perform next?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements.
AHV IPAM assigns an IP address from the address pool when creating a managed VM NIC.
At which two instances does the address release back to the pool? (Choose two)
Refer to the exhibit.
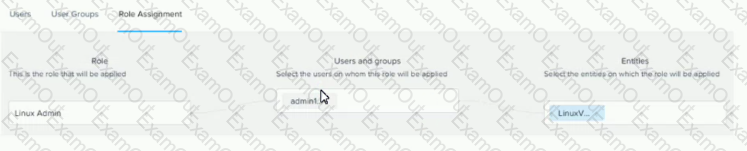
The Linux Admin role has been created to manage only Linux VMs in the environment. However, the Adminl user does not have access to all Linux VMs.
What step should be taken to grant the proper access?
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?