To assist with capacity planning, your supervisor wants to receive weekly capacity summaryreports using e- mail for all on-premises ONTAP clusters. You are asked to implement a solution that has no additional software licensing costs.
Which action accomplishes this task?
A client is planning to configure a SnapMirror relationship between two sites. Normally their ISP provides network throughput of 100 Mbps; however, they can arrange to have this burst to 1 Gbps for a period of time at an additional cost.
Their intention is to back up 400 GB of Snapshot data each day using the burst option to keep the replication time to a minimum. In this scenario, how much burst time do they need to purchase?
Your DevOps team reported that one virtual machine on a VMware datastore has been corrupted due to a ransomware attack.
In this scenario, which two methods would solvethe issue? (Choose two.)
You want to create an application-consistent Snapshot copy by using SnapCenter software. What is required to accomplishthis task?
You are asked to enable WORM technology on a large amount of legal data. The legal team asks that a designated user group have the ability to delete files as needed.
What would satisfy the legal team's requirements?
Click the Exhibit button.
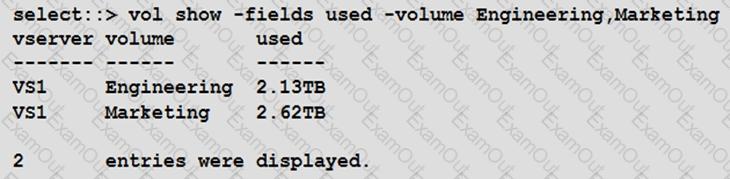
Your customer is deploying SnapCenter to protect volumes on an ONTAP Select cluster.
Referring to the exhibit, which licensing is required to protect the Engineering and Marketing volumes?
What are two NetApp data protection solutions? (Choose two.)
Which two tools would you use toverify that an Oracle database has an application-consistent snapshot taken? (Choose two.)
You want to generate performance-related reports and alerts using the OnCommand Unified Manager 6.x server. Which two additional tasks must be completed to enable these features?
(Choose two.)
Click the Exhibit button.
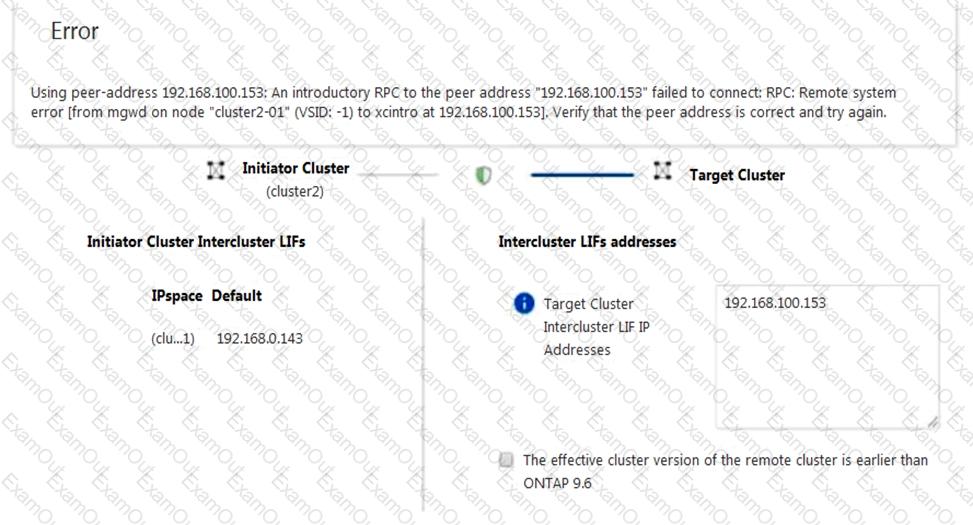
You are configuring cluster peering from cluster2 to cluster1 on your ONTAP 9.7 clusters using ONTAP System Manager. You are given the details shown below to set up the cluster peer relationship. You want to determine why the peering has failed.
Cluster2 intercluster LIFIP: 192.168.0.143 Subnet: 255.255.255.0 Port: e0e passphrase: netapp1234
Cluster1 intercluster LIF IP: 192.168.0.153 Subnet: 255.255.255.0 Port: e0e passphrase: netapp1234
Referring to the exhibit, which statement is correct?

