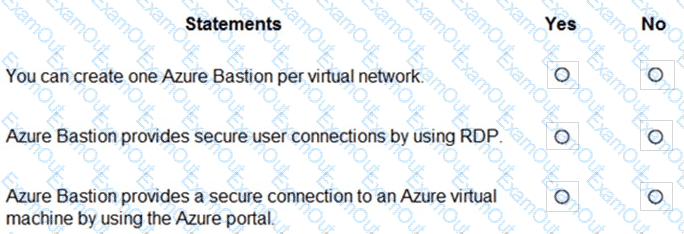
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
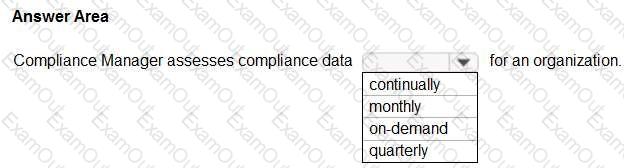
completes the sentence.
What is an example of encryption at rest?
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to create a data loss prevention (DLP) policy. What should you use?
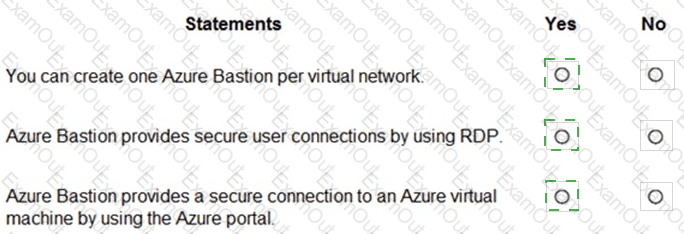
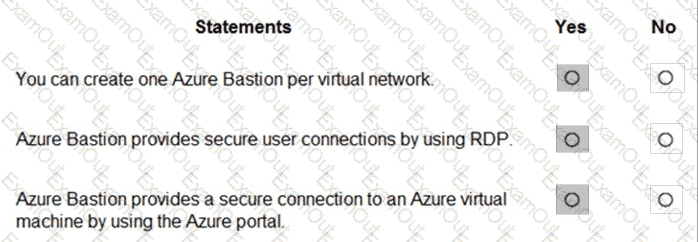
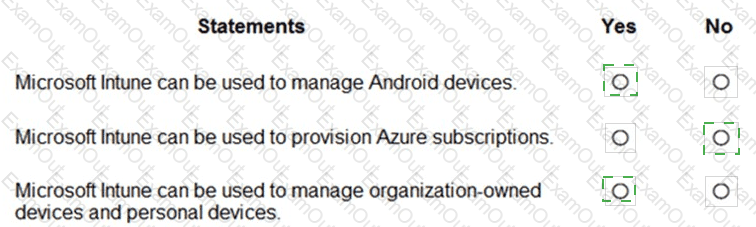
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you specify in Microsoft 365 sensitivity labels?
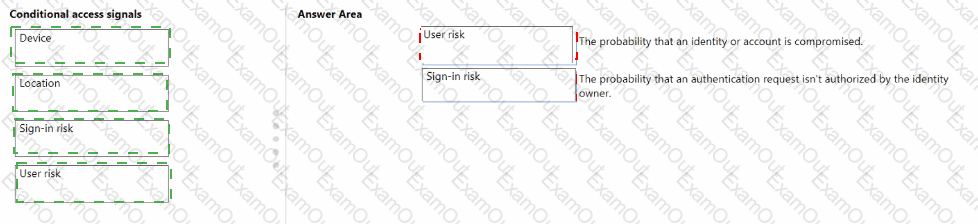
Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

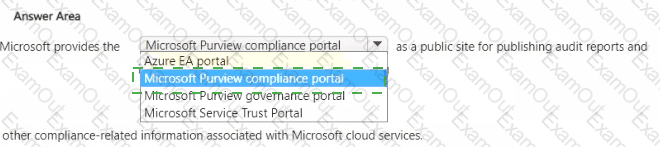
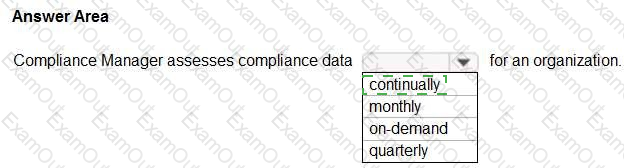
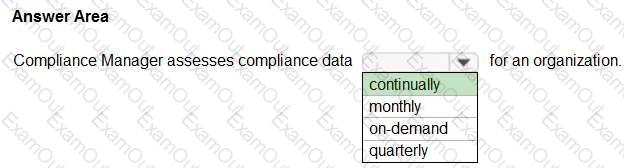
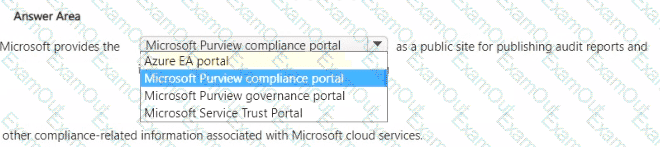
Select the answer that correctly completes the sentence.