You are the Microsoft 365 administrator for a company.
The company runs SharePoint Server and Exchange Server in an on-premises datacenter. The site collection for the finance department is currently encrypted using third party software.
You need to move as many services to Microsoft 365 as possible.
What should you do?
You are a Microsoft 365 administrator for a company.
Several users report that they receive emails which have a PDF attachment. The PDF attachment launches malicious code.
You need to remove the message from inboxes and disable the PDF threat if an affected document is opened.
Which feature should you implement?
A company uses Microsoft 365.
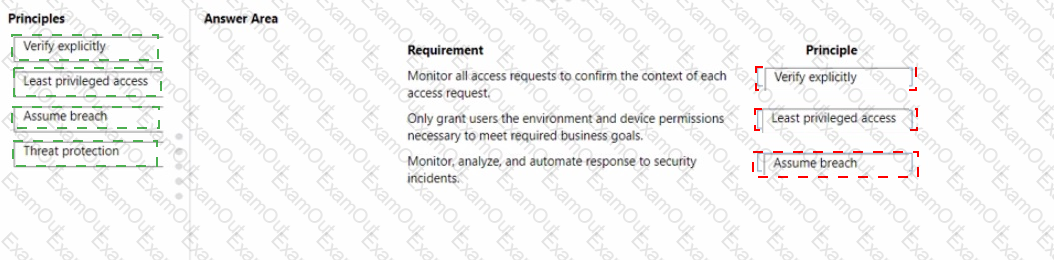
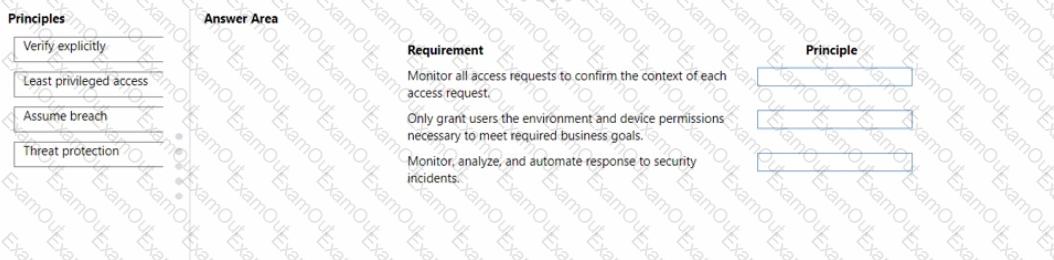
The company is evaluating which Zero Trust security policies to implement.
Which Zero Trust security principle should yourecommend? To answer, drag the appropriate principles to the correct requirements. Each principle may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content
NOTE: Each correct selection I worth one point.
You are the Microsoft 365 administrator for a company.
A user experiences an issue with SharePoint Online.
You need toresolve the issue.
Which two options can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A company plans to deploy Microsoft Viva Insights.
The company has concerns with the privacy of data that is used in Viva Insights.
You need toidentify the source of data that is used in Viva Insights.
What are three data sources of Viva Insights? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A company plans to implement Microsoft 365 to manage projects and appointments with customers.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

A company plans to deploy Microsoft 365.
The company has not deployed any Microsoft products. The company requires a user subscription license (USL) that minimizes license costs.
You need to identify which license solution touse.
Select the answer that correctly completes the sentence.

: 130
You need to ensure that all users in your tenant have access to the earliest release of updates in Microsoft 365. You set the organizational release preference toStandard release.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
You are evaluating Office 365 ProPlus for a company.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

A company is migrating to Microsoft 365.
The company is evaluating app integrations in Microsoft Teams
Which app integrations should you recommend' To answer, drag the appropriate integrations to the correct features. Each integration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point